Tenable Vulnerability Management FAQ
Contents
Try Tenable Vulnerability Management
Run your first scan in under 60 seconds.
General Questions
What is Tenable Vulnerability Management?
Vulnerability Management is a risk-based vulnerability management solution that gives you full network visibility to predict attacks and quickly respond to critical vulnerabilities. Continuous, always-on discovery and assessment provide the visibility you need to find all assets on your network, as well as hidden vulnerabilities on those assets. Built-in prioritization, threat intelligence and real-time reporting help you understand your risk and proactively disrupt attack paths. Built on leading Tenable Nessus technology and managed in the cloud, you get complete visibility of the assets and vulnerabilities on your network so you can quickly and accurately understand your risk and know which vulnerabilities to fix first.
Tenable Vulnerability Management is an integral component of Tenable One, Tenable's Exposure Management Platform. Tenable One builds off of Tenable Vulnerability Management and provides actionable insight into your entire infrastructure's security risks- including cloud instances, web applications, Active Directory (AD) and more, even highly dynamic assets like mobile devices, virtual machines and containers. To elevate cyber risk management even further, you get additional prioritization metrics and capabilities, such as attack surface visualizations, asset criticality ratings, risk-based exposure scoring and peer benchmarking, as well as the ability to track risk reduction over time.
How can I learn more about Tenable Vulnerability Management?
To learn more about Tenable Vulnerability Management, please visit the Tenable Vulnerability Management product page, attend an upcoming webinar or contact your Tenable certified partner or Tenable representative for more information.
How can I evaluate Tenable Vulnerability Management applications?
Please register for a free evaluation of Tenable Vulnerability Management by visiting https://www.tenable.com/try.
How can I buy Tenable Vulnerability Management applications?
You can purchase Tenable Vulnerability Management applications by working with your local Tenable certified partner, contacting your Tenable representative or visiting tenable.com.
Can I license Tenable applications individually?
Yes. You can license Tenable applications individually. For example, Tenable Web App Scanning can be licensed on its own, without the vulnerability management capabilities of Tenable Vulnerability Management.
How is Tenable Vulnerability Management priced and licensed?
A Tenable Vulnerability Managemento is licensed by annual subscription and priced by asset, rather than by IP address. This enables customers to embrace new technologies like cloud without fear of double-counting.
For more information on pricing and licensing, please see the section below.
What is an asset?
An asset is:
- A physical or virtual device with an operating system connected to a network
- A web application with an FQDN
- An active (not terminated) cloud resource
Examples include: desktops, laptops, servers, storage or network devices, phones, tablets, virtual machines, cloud instances and containers, etc.
How are other Tenable Vulnerability Management applications priced and licensed?
Tenable Web App Scanning is licensed by annual subscription and priced by asset quantity. Tenable Web App Scanning is priced by the total number of fully qualified domain names (FQDN) the product assesses.
For more information on pricing and licensing, please see the section below.
Does Tenable offer a service level agreement (SLA) for Tenable Vulnerability Management?
Yes. Tenable provides the vulnerability management industry’s first uptime guarantee through a robust service level agreement (SLA) for Tenable Vulnerability Management. Service credits are offered if the SLA is not met, just like leading cloud vendors, such as Amazon Web Services (AWS).
Where can I find documentation on Tenable Vulnerability Management?
Technical documentation for all Tenable products, including Tenable Vulnerability Management, is at https://docs.tenable.com.
What IPs does Tenable use for scanning from the cloud?
Can I use both Tenable Security Center and Tenable Vulnerability Management?
Yes. You can use both solutions. Customers can choose a hybrid vulnerability management deployment by utilizing both Tenable Security Center and Tenable Vulnerability Management. Customers interested in Tenable Vulnerability Management PCI/ASV, or other Tenable Vulnerability Management applications, can also choose a hybrid deployment alongside their Tenable Security Center instance.
Can I migrate from Tenable Security Center to Tenable Vulnerability Management?
Yes. For customers who are interested, there are a range of options to smoothly migrate from Tenable Security Center to Tenable Vulnerability Management, with full support from Tenable or your certified partner. For more information, please contact your Tenable certified partner or Tenable representative.
What is External Attack Surface Management (EASM)?
External Attack Surface Management (EASM) is a capability Tenable offers that provides visibility into blind spots outside of your network perimeter. This allows you to scan your domain to find previously unknown internet-connected assets that can pose high risk to your organization.
Is External Attack Surface Management (EASM) included in Tenable Vulnerability Management?
Yes, Tenable Vulnerability Management offers External Attack Surface Management (EASM) capabilities. If you require additional domains, frequency and/or metadata in your results, you can purchase our Tenable Attack Surface Management add-ons.
What is Tenable Web App Scanning?
Tenable Web App Scanning is a dynamic application security testing (DAST) application. A DAST crawls a running web application through the front end to create a site map with all of the pages, links and forms for testing. Once the DAST creates a site map, it interrogates the site through the front end to identify any vulnerabilities in the application custom code or known vulnerabilities in the third-party components that comprise the bulk of the application
Where can I learn more about or evaluate Tenable Web App Scanning?
For more information about Tenable Web App Scanning, please visit Tenable Web App Scanning product page. Please register for a free evaluation by visiting tenable.com/try-was or contact your Tenable certified partner or Tenable representative for more information.
Does the product scan source code or perform static analysis?
No. Tenable Web App Scanning is a dynamic application security testing (DAST) solution that tests a web application “from the outside” when the application is running in a test or production environment.
Elastic Asset Licensing Questions
Elastic Asset Licensing, built into Tenable Vulnerability Management, is an innovation that aligns vulnerability management licensing with today’s elastic IT environments. Elastic Asset Licensing avoids double counting assets that have multiple and/or changing IP addresses. Additionally, it automatically reclaims licenses from assets that have not been recently scanned, including retired assets and assets that may have been inadvertently scanned.
What is Tenable Vulnerability Management Elastic Asset Licensing?
The primary benefits of Elastic Asset Licensing are:
- Customers purchase the right amount of licenses, based on asset quantities, not inflated IP counts.
- Customers avoid time-consuming and often inaccurate projects needed to reclaim licenses from decommissioned and/or inadvertently scanned assets.
- Vulnerability management metrics are not corrupted by double and triple counting vulnerabilities for assets that have multiple IP addresses.
What are the benefits of Elastic Asset Licensing?
The primary benefits of Elastic Asset Licensing are:
- Customers purchase the right amount of licenses, based on asset quantities, not inflated IP counts.
- Customers avoid time-consuming and often inaccurate projects needed to reclaim licenses from decommissioned and/or inadvertently scanned assets.
- Vulnerability management metrics are not corrupted by double and triple counting vulnerabilities for assets that have multiple IP addresses.
Can Tenable Vulnerability Management customers scan more assets than licensed?
Yes, on a temporary basis, customers can exceed the licensed number of assets. Of course, customers need to true-up when license counts continue to be exceeded.
How can Tenable Vulnerability Management customers determine license status?
The Tenable Vulnerability Management user interface displays both the licensed number of assets and the actual license usage.
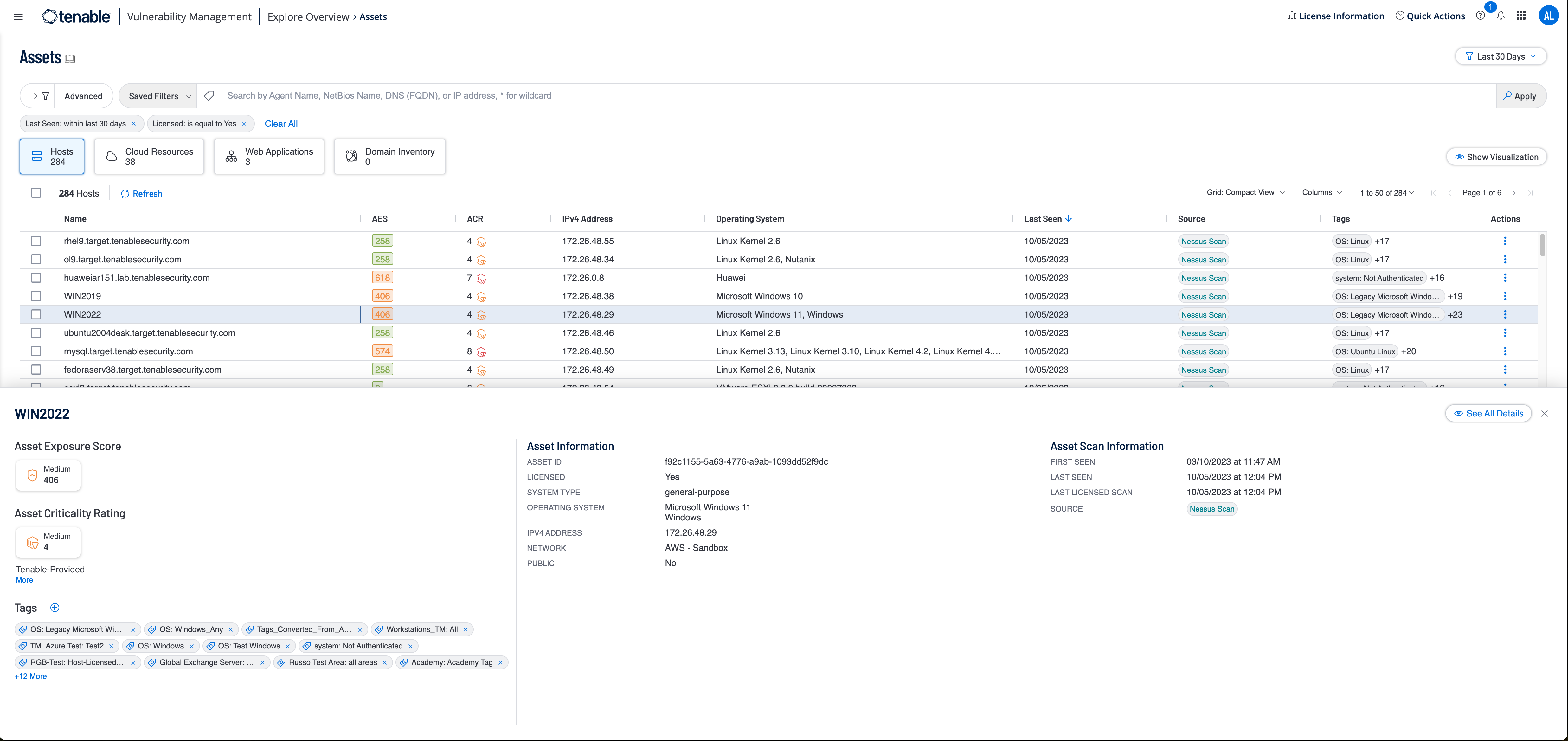
What is an asset?
An asset is an entity that can be analyzed. Examples include desktops, laptops, servers, storage devices, network devices, phones, tablets, VMs, hypervisors and containers.
How does Tenable Vulnerability Management identify an asset?
When Tenable Vulnerability Management first discovers an asset, it gathers multiple identification attributes, which may include a BIOS UUID, the system’s MAC Address, NetBIOS name, FQDN, and/or other attributes that can be used to reliably identify an asset. Additionally, authenticated scanning and Nessus agents assign a Tenable UUID to the device. When Tenable Vulnerability Management subsequently scans an asset, it compares it to previously discovered assets. If the newly discovered asset does not match a previously discovered asset, the asset is added to the Tenable Vulnerability Management asset inventory.
How are assets different from IPs?
IPs are typically a property of an asset, and many assets have multiple IPs assigned (such as DHCP devices, systems with both wired and wireless interfaces, etc.).
Why are asset counts likely to be lower than IP counts?
Frequently, assets have multiple network interface cards, enabling them to be accessed by multiple networks. As examples, a web server may have simultaneously been on a production network and an administrative network, or a laptop will often have both a wired and wireless network interface. Additionally, laptops often get new IPs as they move from one location to another. If they are scanned with one IP and then another, they will be counted twice.
How can prospects estimate their asset count?
Tenable Vulnerability Management supports unlimited discovery scans using both active and passive sensors. Customers can use these scans to comprehensively inventory all of their assets and determine the appropriate license size.
How do you avoid counting the same asset multiple times?
Tenable Vulnerability Management supports a variety of methodologies to avoid double- or triple- counting the same asset for calculating the appropriate licensing size. With traditional assets, Tenable Vulnerability Management uses a proprietary algorithm that matches newly discovered assets with already discovered assets to eliminate duplicates and ensure more accurate vulnerability reporting.
Data Security and Privacy Questions
Customer data security and privacy is the top priority of Tenable. Thousands of customers, including financial service providers, healthcare providers, retailers, educational institutions and government agencies trust Tenable with their vulnerability data in our cloud platform.
Data security and privacy include not allowing customers to access any data other than their own and ensuring that any non-customer, hacker, bad actor or unauthorized Tenable representative cannot access, disclose, copy or otherwise violate the privacy and protection of the customers' data stored in the Tenable Vulnerability Management service.
Tenable also focuses on the availability and reliability of the Tenable Vulnerability Management service because poor security controls can create problems that, while not a risk to customers’ data, can affect the service availability. Tenable implements and enforces measures to make Tenable Vulnerability Management highly available, guarded against attacks or simple faults and outages, and always usable for our customers.
What customer data does Tenable Vulnerability Management manage?
Ultimately, the customer data Tenable Vulnerability Management manages has a single purpose: to deliver an exceptional experience as customers manage assets and vulnerabilities to secure their environments. To that end, Tenable Vulnerability Management manages three categories of customer data:
- Asset and vulnerability data
- Environmental performance data
- Customer usage data
What customer asset and vulnerability data does Tenable Vulnerability Management manage?
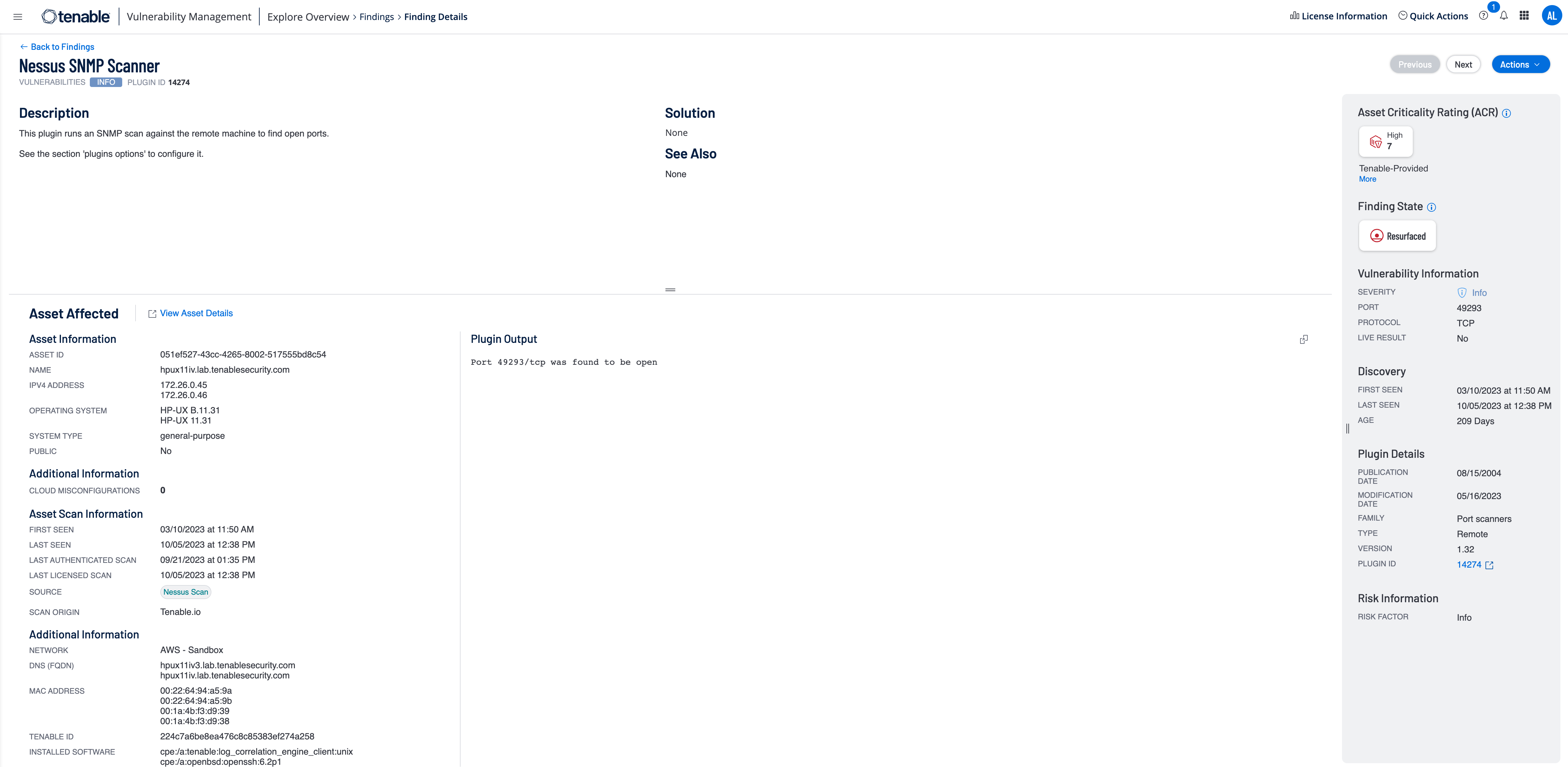
Tenable Vulnerability Management inventories assets on customers’ networks and manages asset attributes that may include IP address, MAC address, NetBIOS name, operating system and version, active ports and more.
Tenable Vulnerability Management collects detailed current and historical vulnerability and configuration data, which may include criticality, exploitability and remediation status and network activity. Additionally, if customers enhance Tenable Vulnerability Managemento data with integrations to third-party products, such as asset management systems and patch management systems, Tenable Vulnerability Management may manage data from those products.
Does Tenable analyze or use customer data?
Tenable anonymizes and analyzes customer data for the purpose of determining trends in the industry, trends in vulnerability growth and mitigation, and trends in security events. For example, correlating the presence of a vulnerability with its exploitation has enormous benefits to Tenable customers. Additional benefits include advanced analytics and improved correlation of customer data with industry and security events and trends. Collecting and analyzing such data also allows customers to baseline themselves against others in the industry or overall. Tenable provides a method for customers to opt out if desired.
What Tenable Vulnerability Management health and status data is collected?
To maintain Tenable Vulnerability Management performance and availability and deliver the best possible user experience, Tenable Vulnerability Management collects customer-specific application status and health information. This includes how often the scanner communicates to the platform, the number of scanned assets and versions of software deployed, as well as other general telemetry to identify and address potential issues as soon as possible.
Can customers opt out of health and status data collection?
Tenable uses health and status data to detect and address potential issues in a timely manner, thereby maintaining SLA commitments. Therefore, customers cannot opt out of this data collection.
What Tenable Vulnerability Management usage data is collected?
To evaluate and improve customer experience, Tenable collects anonymized user usage data. This data includes page access, clicks and other user activity which give the user a voice into streamlining and improving the user experience.
Can users opt out of usage data collection?
Yes. A customer can request that their container no longer be part of the collection process.
Where is customer data located?
Tenable uses data centers and services from Amazon Web Services (AWS) to provide and deliver Tenable Vulnerability Management to customers. By default, Tenable will choose to create a customer container in the region that is most appropriate to ensure the best possible experience for that customer. Current locations are:
- U.S. East
- U.S West
- U.S Central
- London
- Frankfurt
- Sydney
- Singapore
- Canada
- Japan
- Brazil
- India
By exception, if prior to deployment, a customer requests a specific AWS region, Tenable will activate the customer in that region.
As all customer data is stored in secure, regional AWS services, the certifications for EU data protection that AWS maintains apply to the Tenable Cloud. More information is available here.
Will Tenable Vulnerability Managemento support additional countries in the future? If so, what is the timeframe?
Yes. However, the timeframe of additional locations is not yet determined.
Can data be stored in AWS regions other than the original region?
There are situations where data could be stored in regions other than the initial AWS region.
- Tenable Vulnerability Management customers can run external scans using the public, shared scanning pools available in a number of AWS regions. Choosing a scanner close to the target will generally result in faster scans. Note that when a customer uses a cloud scanner in a different locality than the one hosting their account, scan data will temporarily exist outside the account’s hosting locality, but it is not stored. For example, if a customer with an account hosted in EU/Germany scans with a scanner in US/N. Virginia, the scan data will temporarily pass through the USA before being stored in Frankfurt. If data locality is an issue, customers should only do external scans with cloud scanners in their region. This is easily selectable on a per-scan basis.
- If a customer is using Tenable Security Center, their scan data is not stored in the cloud, even if they are using Tenable Vulnerability Management to scan part of their entire infrastructure.
- Tenable Nessus Agent scan data is stored in Tenable Vulnerability Management when customers run scans from Tenable Vulnerability Management. If customers are running agent scans with Tenable Nessus Manager, that data will not be stored in Tenable Vulnerability Management, regardless of where the agents are deployed.
Can a customer force data to remain in a specific location/country?
Yes. Data is stored in the country selected when the account was created.
How is customer data protected within Tenable Vulnerability Management?
Tenable applies multiple security measures to deliver Tenable Vulnerability Management data security and privacy.
How does Tenable perform secure development?
Tenable follows a number of practices to ensure security of Tenable Vulnerability Management application software.
Testing is done by three separate groups within Tenable:
- Security testing is done by the development team;
- The Tenable IT Security team performs vulnerability testing on Tenable Vulnerability Management both before and after deployment (post-deployment tests are unscheduled with no advance warning to other teams); and
- Tenable provides additional security review of source code and changes prior to deployment.
All software deployment is automated and performed only via the build system, which is authenticated via corporate LDAP credentials or by Ansible, which is authenticated using SSH private keys. All deployments are logged and tracked, and notification of deployment action (planned or unplanned) is automatically sent to the Tenable development team.
All changes to the source code are tracked and linked to the release where that change gets installed. This tracking ensures that there is a complete history of every change, who made it, when it was made, and finally, when the change was deployed into production.
Each deployment is approved by at least two Tenable team members. All changes and deployments are broadcast to all team members. Software is first deployed to test environments, and then deployed in a "rolling fashion" to production instances over a window of time.
What customer application security is available?
- Ensuring access to Tenable Vulnerability Management in a secure and authorized manner is a high priority for our development and operations teams. Tenable Vulnerability Management provides a number of mechanisms to keep customer data secure and control access. We protect against brute force attacks by locking accounts out after five (5) failed login attempts.
- To protect from data interceptions all communication to the platform is encrypted via SSL (TLS-1.2). Further, older insecure SSL negotiations are rejected to ensure the highest level of protection.
- To protect access to the platform, customers can configure two-factor authentication through services provided by Twillo.
- Customers can integrate Tenable Vulnerability Management with their SAML deployment. Tenable Vulnerability Management supports both IdP and SP initiated requests. Lastly, users can reset their password directly inside of the application using their email address.
- Customers often build customer connections to Tenable Vulnerability Management using our documented APIs or SDKs. Access can be granted and controlled by the creation of specific APIs "keys.” Using different keys for different integrations is supported without having to share user credentials.
How is customer data protected?
Tenable applies multiple security measures to deliver Tenable Vulnerability Management data security and privacy.
How is data encrypted?
All data in all states in the Tenable Vulnerability Management platform is encrypted with at least one level of encryption, using no less than AES-256.
At Rest: Data is stored on encrypted media using at least one level of AES-256 encryption.
Some data classes include a second-level of per-file encryption.
In Transport: Data is encrypted in transport using TLS v1.2 with a 4096-bit key (this includes internal transports).
Tenable Vulnerability Management Sensor Communication: Traffic from the sensors to the platform is always initiated by the sensor and is outbound-only over port 443. Traffic is encrypted via SSL communication using TLS 1.2 with a 4096-bit key. This removes the need for firewall changes and allows the customer to control the connections via firewall rules.
- Scanner-to-platform authentication
- The platform generates a random key of 256 bit length for each scanner connected to the container and passes that key to scanner during the linking process
- Scanners uses this key to authenticate back to the controller when requesting jobs, plugin updates and updates to the scanner binary
- Scanner-to-platform job communication
- Scanners contact the platform every 30 seconds
- If there is a job, the platform generates a random key of 128-bits
- The scanner requests the policy from the platform
- The controller uses the key to encrypt the policy, which includes the credentials to be used during the scan
In Backups/Replication: Volume snapshots and data replicas are stored with the same level of encryption as their source, no less than AES-256. All replication is done via the provider. Tenable does not back up any data to physical off-site media or physical systems.
In Indexes: Index data is stored on encrypted media using at least one level of AES-256 encryption.
Scan Credentials: Are stored inside of a policy which is encrypted within the containers AES-256 global key. When scans are launched the policy is encrypted with a one use random 128-bit key and transported using TLS v1.2 with a 4096-bit key.
Key Management: Keys are stored centrally, encrypted with a role-based key, and access is limited. All the encrypted data stored can be rotated to a new key. The datafile encryption keys are different on each regional site, as are the disk-level keys. Sharing of keys is prohibited and key management procedures are reviewed on a yearly basis.
Can customers upload their own keys?
Key management is not customer configurable. Tenable manages the keys and key rotation.
Has Tenable achieved any privacy or security certifications, such as Privacy Shield or CSA STAR?
Tenable Network Security complies with the EU-U.S. Privacy Shield Framework and the Swiss – U.S. Privacy Shield Framework as set forth by the U.S. Department of Commerce regarding the collection, use and retention of personal information transferred from the European Union and Switzerland to the United States, respectively. Tenable Network Security has certified to the Department of Commerce that it adheres to the Privacy Shield Principles. If there is any conflict between the terms in this privacy policy and the Privacy Shield Principles, the Privacy Shield Principles shall govern. To learn more about the Privacy Shield program, and to view our certification, please visit https://www.privacyshield.gov/.
Tenable has completed the Cloud Security Alliance (CSA) STAR self-assessment. Tenable responses to the Consensus Assessment Initiative Questionnaire (CAIQ) answer a set of over 140 security related questions a Tenable Vulnerability Management prospect, customer or partner may require. CSA STAR is the industry’s most powerful program for security assurance in the cloud. STAR (Security Trust & Assurance Registry) encompasses key principles of transparency, rigorous auditing, and harmonization of standards, including indications of best practices and validation of security posture of cloud offerings.
How is personally identifiable information (PII) protected?
The Tenable Vulnerability Management platform makes every effort not to collect personally identifiable information (PII) data types in a format that would require additional certifications or security measures. This includes credit card numbers, Social Security numbers and other custom checks. Where Tenable plug-ins capture character strings that may contain sensitive or personal information, the platform will automatically obfuscate at least 50% of the characters to protect data that may be sensitive.
Is customer data separated?
Each customer’s data is marked with a "container ID,” which corresponds to a specific customer subscription. This container ID assures that access to a customer’s data is limited to only that customer.
What security controls protect Tenable Vulnerability Management?
- Tenable performs daily vulnerability scans.
- Firewalls and network segmentation control access. Automated tools and processes monitor the Tenable Vulnerability Management platform for uptime, performance and to detect anomalous behavior.
- Logs are monitored with automation 24/7/365 and Tenable staff are available 24/7/365 to respond to events.
How are Tenable Vulnerability Management sensors secured?
The sensors that connect to the platform play a major role in a customer’s security, collecting vulnerability and asset information. Protecting this data and ensuring the communication paths are secure is a core function of the Tenable Vulnerability Management. Tenable Vulnerability Management supports several sensors today: Tenable Nessus vulnerability scanners, passive scanners and Tenable Nessus Agents.
These sensors connect to the Tenable Vulnerability Management platform after cryptographically authenticating and linking to Tenable Vulnerability Management. Once linked, Tenable Vulnerability Management manages all updates (plugins, code, etc.) to ensure the sensors are always up to date.
Traffic from the sensors to the platform is always initiated by the sensor and is outbound-only over port 443. Traffic is encrypted via SSL communication using TLS 1.2 with a 4096-bit key. This removes the need for firewall changes and allows the customer to control the connections via firewall rules.
- Scanner-to-platform authentication
- The platform generates a random key of 256 bit length for each scanner connected to the container and passes that key to scanner during the linking process
- Scanners uses this key to authenticate back to the controller when requesting jobs, plugin updates and updates to the scanner binary
- Scanner-to-platform job communication
- Scanners contact the platform every 30 seconds
- If there is a job, the platform generates a random key of 128-bits
- The scanner requests the policy from the platform
- The controller uses the key to encrypt the policy, which includes the credentials to be used during the scan
How is Tenable Vulnerability Management availability managed?
The Tenable Vulnerability Management services strive to provide a 99.95% or better uptime, and have delivered 100% uptime on the majority of services. Tenable has published an SLA which describes our commitment to ensure the platform is available to all users and how we credit customers in the event of unplanned downtime.
"Up" status is determined simply by public availability tests hosted by a third party that regularly test the availability of all the services. The uptime for the services (both current and historical) is available at https://status.tenable.com.
Tenable Vulnerability Management makes extensive use of the AWS platform and other leading technologies to ensure our customers experience the best possible service and overall quality. Below is a partial list of the solutions deployed the benefits to customers
- ElasticSearch clusters: Elasticsearch clusters are highly available and can recover from the loss of master nodes, lb nodes and at least 1 data node, without impacting service availability.
- Elastic block stores: Used to take daily snapshots and store eight (8) copies.
- Kafka ecosystem: Kafka and Zookeeper both replicate data across the cluster to provide fault tolerance given catastrophic failure of any node.
- Postgres Instances: Manages the back-end microservice framework to keep 30 days of snapshots.
Where is data replicated?
Replicated data is stored within the same region.
What disaster recovery capabilities are in place?
Disasters are events that result in the unrecoverable loss of data or equipment in one or more regions.
Tenable Vulnerability Management disaster recovery procedures have several levels and are designed to react to situations that may occur from anywhere between once in five years to once in 50 years. Depending on the scope of the disaster, the recovery procedures vary in time from 60 minutes to 48 hours.
Who can access customer data?
Customers control who has access to their data, including assigning roles and permissions to their personnel and temporarily granting access from Tenable support staff.
How are user roles and permissions managed?
Tenable Vulnerability Management customer administrators can assign user roles (basic, standard, administrator and disabled) to manage access to scans, policies, scanners, agents and asset lists.
Can Tenable staff access customer data?
Yes. With customer permission, tier three members of Tenable’s global support staff can impersonate user accounts, which allows them to perform operations in Tenable Vulnerability Management as another user without needing to obtain that user's password. Tenable support staff, or the customer, can make the request to activate the feature. Tenable support staff requires the customer to “approve” the impersonation via a note in an active support case. Permission must be granted for every issue logged with support. Tenable will not operate on a blanket “OK” to impersonate at any time. User impersonation may result in data leaving the primary location.
All Tenable Vulnerability Management operations staff are required to pass a third-party background check. In addition, all senior team members have at least five years of experience at SaaS-based security software companies and many carry security certifications, such as CISSP.
Tenable has a defined hiring and termination process. All employees are required to sign non-disclosure agreements as a part of their hiring, and all accounts and access keys are immediately revoked upon termination.
Who can use the impersonate function?
Only Tenable tier three support staff members are allowed to use the impersonate function.
Is impersonation activity logged?
Yes.
Does the data leave the country when Tenable is troubleshooting a technical issue?
Tenable is making every effort to ensure that customer data is protected and we ensure their policies are being followed by working with customers to ensure the data remains in the region required. However, there are instances where customers could email a report to Tenable or otherwise break their own policy emailing outside of their region.
Will Tenable support staff have access to a customer’s internal network?
No. All traffic is initiated by the scanner and is outbound only. The scanners are installed behind the customer's firewall and can control the access of the scanners via their firewall.
How long is customer data retained within Tenable Vulnerability Management?
Data retention periods are designed to meet various customer and regulatory requirements.
How long is active scan data retained?
The ability to measure progress over time is a core function of the Tenable Vulnerability Management platform. Tenable Vulnerability Management will automatically store customer data for 15 months to allow them to report over a one (1) year period of time.
If customers need longer than 15 months of storage, Tenable Vulnerability Management provides several methods to download customer data and customers can store it as they wish.
If a customer discontinues the Tenable Vulnerability Management service, how long is data retained?
Should a customer's account expire or terminate, Tenable will retain the data, as it was at the time of expiration, for no more than 180 days. After that time, this data may be deleted and cannot be recovered.
How long is PCI-related data retained?
Data which is involved in a PCI compliance validation process is not deleted until at least three years after the date of the PCI attestation, as required by PCI regulations. Tenable retains this data for this time period, even if the customer chooses to delete their scans or account, or terminates their Tenable Vulnerability Management service.
How long is Tenable Vulnerability Management usage data retained?
In order to ensure the best possible experience, we are collecting this information as long as a customer container remains active. Once a customer discontinues the service, the data will be retained for no more than 180 days.
Does Tenable Vulnerability Management have Common Criteria certification?
Common Criteria certification is generally not applied to a SaaS solution, as the frequency of updates does not lend itself to a certification process that takes six to nine months to complete.
Can a customer choose the country where that data is stored?
By exception, if prior to deployment, a customer requests a specific geographic location, Tenable will activate the customer in that location. Current locations are:
- U.S.
- London
- Frankfurt
- Sydney
- Singapore
- Canada
- Japan
- Brazil
- India
Does data exist in multiple locations within a country?
No. Tenable does not currently replicate data from one location to another.
PCI ASV
What is PCI ASV?
PCI ASV refers to requirement 11.2.2 of the Payment Card Industry (PCI) Data Security Standard (DSS) Requirements and Security Assessment Procedures that requires quarterly external vulnerability scans, which must be performed (or attested to) by an Approved Scanning Vendor (ASV). An ASV is an organization with a set of services and tools (“ASV Scanning Solution”) to validate adherence to the external scanning requirement of PCI DSS Requirement 11.2.2.
Which systems are in scope for ASV Scanning?
The PCI DSS requires vulnerability scanning of all externally accessible (internet-facing) system components owned or utilized by the scan customer that are part of the cardholder data environment, as well as any externally facing system component that provides a path to the cardholder data environment.
What is the ASV process?
The main phases of ASV scanning consist of:
- Scoping: Performed by the customer to include all internet-facing system components that are part of the cardholder data environment.
- Scanning: Using the Tenable Vulnerability Management PCI Quarterly External Scan template
- Reporting/remediation: Results from interim reports are remediated.
- Dispute resolution: Customer and ASV work together to document and resolve disputed scan results.
- Rescan (as needed): Until a passing scan that resolves disputes and exceptions is generated.
- Final reporting: Submitted and delivered in a secure fashion.
How frequently are ASV scans required?
ASV vulnerability scans are required at least quarterly and after any significant change in the network, such as new system component installations, changes in network topology, firewall-rule modifications or product upgrades.
How is an approved scanning vendor (ASV) different from a qualified security assessor (QSA)?
An approved scanning vendor (ASV) specifically performs only the external vulnerability scans described in PCI DSS 11.2. A qualified security assessor (QSA) refers to an assessor company the PCI Security Standards Council (SSC) has qualified and trained to perform general PCI DSS on-site assessments.
Tenable PCI ASV Solution Capabilities
Is Tenable a certified PCI ASV?
Yes. Tenable is qualified as an approved scanning vendor (ASV) to validate external vulnerability scans of internet-facing environments (used to store, process or transmit cardholder data) of merchants and service providers. The ASV qualification process consists of three parts: the first involves the qualification of Tenable Network Security as a vendor. The second relates to the qualification of Tenable employees responsible for the remote PCI scanning services. The third consists of the security testing of the Tenable remote scanning solution (Tenable Vulnerability Management and Tenable PCI ASV).
As an approved scanning vendor (ASV), does Tenable actually perform the scans?
ASVs may perform the scans. However, Tenable relies on customers to conduct their own scans using the PCI Quarterly External Scan template. This template prevents customers from changing configuration settings, such as disabling vulnerability checks, assigning severity levels, altering scan paraments, etc. Customers use Tenable Vulnerability Management cloud-based scanners to scan their internet-facing environments and then submit compliant scan reports to Tenable for attestation. Tenable attests the scan reports, and then the customer submits them to their acquirers or payment brands as directed by the payment brands.
Data Sovereignty
Does Tenable PCI ASV comply with EU data sovereignty requirements?
Vulnerability data is not EU DPD 95/46/EC data, so any data residency requirements would be customer, not regulatory driven. EU state governmental organizations could have their own data residency requirements, but those would have to be assessed on a case-by-case basis and probably not an issue for PCI-ASV scans.
Tenable Vulnerability Management ASV Pricing/Licensing/Ordering
Does Tenable Vulnerability Management include any PCI ASV licenses?
Yes, Tenable Vulnerability Management includes a PCI ASV license for a single, unique PCI asset. Some organizations have taken great pains to limit the assets in scope for PCI, often by outsourcing payment processing functions. Because these customers are arguably "not in the PCI business," Tenable has simplified its purchasing and licensing. A customer can change their asset every 90 days.
How is Tenable PCI ASV licensed?
For customers having more than a single, unique PCI asset, the Tenable PCI ASV solution is licensed as an add-on to Tenable Vulnerability Management subscriptions.
Why isn’t Tenable PCI ASV licensed according to the number of a customer’s internet-facing PCI assets?
The number of internet-facing hosts that are within or provide a path to an entity’s cardholder data environment (CDE) can change frequently, thereby creating licensing complexity. Tenable elected to use a simpler licensing approach.
How many attestations may a customer submit per quarter?
Customers can submit an unlimited number of quarterly attestations.
Are trial/evaluation customers eligible to evaluate Tenable PCI ASV?
Yes. An evaluation customer can use the PCI Quarterly External Scan template to scan assets and review results. However, they cannot submit the scan reports for attestation.