Bedrohungen entwickeln sich weiter – in der Cloud und On-Prem
Cyberrisiken proaktiv erkennen und beheben
Wenn Ihr Sicherheitsteam nur begrenzten Einblick in die Cloud hat, kann es die Frage „Wie sicher sind wir?“ nicht beantworten. Die Exposure-Management-Plattform von Tenable verschafft Ihnen Einblick in Ihre gesamte Angriffsüberfläche – und zwar mit geschäftlichem Kontext –, sodass Sie Ihre Cyberrisiken genau erkennen und Prioritäten bei der Risikominderung setzen können.
Sichtbarkeit erweitern. Maßnahmen priorisieren. Risiken kommunizieren.
Die Absicherung Ihrer Cloud ist nicht möglich, wenn Sie nicht alle Ihre Assets sehen können. Von Schwachstellen-Management über Cloud-Sicherheit und Identitätssicherheit bis hin zu External Attack Surface Management und mehr – verschaffen Sie sich den nötigen Kontext, um auf der Grundlage Ihres tatsächlichen Cyberrisikos fundiertere Entscheidungen zu treffen.
Proaktive Lösungen für gängige Cybersecurity-Herausforderungen
Cloud-Sicherheit
Verwaltung von Multi-Cloud-Sicherheit und Berechtigungen vereinfachen
Die schnelle Einführung von Cloud-Technologien bedeutet, dass Sie komplexe Multi-Cloud-Umgebungen verwalten müssen. Jedoch kann es sein, dass Sie nicht in alles Einblick haben, was sich in der Cloud befindet. Tenable Cloud Security bietet umfassende Asset-Erfassung, tiefgreifende Risikoanalyse, Bedrohungserkennung zur Laufzeit und Compliance-Unterstützung. So können Sie die Komplexität der Cloud reduzieren, Ihr Cyber-Risiko minimieren und Least Privilege in großem Umfang durchsetzen.
Demo anfordern Mehr erfahrenSchwachstellenmanagement
Nutzen Sie risikobasierte Priorisierung von Schwachstellen
Die heutige IT-Landschaft ist so komplex und verändert sich derart schnell, dass es unmöglich sein kann, herauszufinden, welche Schwachstellen tatsächlich eine Bedrohung für Ihr Unternehmen darstellen. Wenn Sie immer noch veraltete Tools für das Schwachstellen-Management verwenden, werden Sie niemals Schritt halten können. Tenable Vulnerability Management ermöglicht die kontinuierliche Bewertung Ihrer Angriffsoberfläche in Echtzeit. Sie erhalten einen risikobasierten, von Forschungsergebnissen untermauerten Überblick über alle Ihre Schwachstellen, sodass Sie wissen, welche Sie zuerst beheben müssen - einschließlich Best-Practice-Empfehlungen, die Sie zum Ziel führen.
Kostenlos testen Mehr erfahrenOT-Sicherheit
Sichtbarkeit über IT- und OT-Umgebungen hinweg ausweiten
Im Zuge der immer schneller voranschreitenden digitalen Transformation führen integrierte IT- und OT-Umgebungen zu einer größeren Angriffsoberfläche und blinden Flecken. Ohne einen umfassenden Einblick in alle Ihre Systeme und Assets können sich Cyberangriffe leicht in Ihrem Unternehmen ausbreiten. Tenable OT Security bietet umfassende Sichtbarkeit, einheitliche Sicherheit und priorisiertes Bedrohungsmanagement, um Risiken zu minimieren.
Demo anfordern Mehr erfahrenActive Directory-Sicherheit
Active Directory härten und Angriffspfade in Ihrer Umgebung beseitigen
Hinter nahezu jeder Datenpanne in den Schlagzeilen steckt ein Angriff auf Active Directory (AD). AD-Fehlkonfigurationen und andere Sicherheitsprobleme ermöglichen es Angreifern, sich Zugang zu verschaffen, ihre Privilegien zu erhöhen und sich seitwärts durch Ihre gesamte Umgebung zu bewegen – oftmals unbemerkt. Tenable Identity Exposure verschafft Ihnen vollständigen Einblick in Ihre komplexe Active Directory-Umgebung, priorisiert die größten Risiken für Ihr Unternehmen und unterstützt Sie bei deren Behebung, um Angriffspfade proaktiv zu beseitigen, bevor Angreifer sie ausnutzen können.
Kostenlos testen Mehr erfahrenExternal Attack Surface Management
Absicherung Ihrer gesamten externen Angriffsoberfläche
Je mehr Assets, Services und Anwendungen mit Internetzugang Ihr Unternehmen einsetzt, desto größer wird Ihr Cyberrisiko, und oftmals bestehen blinde Flecken, von deren Existenz niemand Kenntnis hat. Dadurch wird Ihre externe Angriffsoberfläche zu einer Ihrer größten Bedrohungen. Tenable Attack Surface Management bildet das gesamte Internet kontinuierlich ab und erfasst Verbindungen zu Ihren internetfähigen Assets, damit Sie Ihre externen Risiken minimieren können.
Kostenlos testen Mehr erfahrenSchwachstellenbewertung
Schwachstellen schnell und präzise aufspüren und beheben
Ihre Schwachstellen zu kennen, ist eine Grundvoraussetzung für das Exposure-Management, und Nessus, der Goldstandard in Sachen Schwachstellenbewertung, ist das Herzstück von Tenable One. Zehntausende von Unternehmen weltweit vertrauen auf Nessus für die Analyse ihrer modernen Angriffsoberflächen. Die Lösung liefert ein präzises Bild, dass Ihnen hilft, Ihre Arbeit schnell und effektiv zu erledigen.
Kostenlos testen Mehr erfahrenVerwaltung von Multi-Cloud-Sicherheit und Berechtigungen vereinfachen
Die schnelle Einführung von Cloud-Technologien bedeutet, dass Sie komplexe Multi-Cloud-Umgebungen verwalten müssen. Jedoch kann es sein, dass Sie nicht in alles Einblick haben, was sich in der Cloud befindet. Tenable Cloud Security bietet umfassende Asset-Erfassung, tiefgreifende Risikoanalyse, Bedrohungserkennung zur Laufzeit und Compliance-Unterstützung. So können Sie die Komplexität der Cloud reduzieren, Ihr Cyber-Risiko minimieren und Least Privilege in großem Umfang durchsetzen.
Demo anfordern Mehr erfahrenNutzen Sie risikobasierte Priorisierung von Schwachstellen
Die heutige IT-Landschaft ist so komplex und verändert sich derart schnell, dass es unmöglich sein kann, herauszufinden, welche Schwachstellen tatsächlich eine Bedrohung für Ihr Unternehmen darstellen. Wenn Sie immer noch veraltete Tools für das Schwachstellen-Management verwenden, werden Sie niemals Schritt halten können. Tenable Vulnerability Management ermöglicht die kontinuierliche Bewertung Ihrer Angriffsoberfläche in Echtzeit. Sie erhalten einen risikobasierten, von Forschungsergebnissen untermauerten Überblick über alle Ihre Schwachstellen, sodass Sie wissen, welche Sie zuerst beheben müssen - einschließlich Best-Practice-Empfehlungen, die Sie zum Ziel führen.
Kostenlos testen Mehr erfahrenSichtbarkeit über IT- und OT-Umgebungen hinweg ausweiten
Im Zuge der immer schneller voranschreitenden digitalen Transformation führen integrierte IT- und OT-Umgebungen zu einer größeren Angriffsoberfläche und blinden Flecken. Ohne einen umfassenden Einblick in alle Ihre Systeme und Assets können sich Cyberangriffe leicht in Ihrem Unternehmen ausbreiten. Tenable OT Security bietet umfassende Sichtbarkeit, einheitliche Sicherheit und priorisiertes Bedrohungsmanagement, um Risiken zu minimieren.
Demo anfordern Mehr erfahrenActive Directory härten und Angriffspfade in Ihrer Umgebung beseitigen
Hinter nahezu jeder Datenpanne in den Schlagzeilen steckt ein Angriff auf Active Directory (AD). AD-Fehlkonfigurationen und andere Sicherheitsprobleme ermöglichen es Angreifern, sich Zugang zu verschaffen, ihre Privilegien zu erhöhen und sich seitwärts durch Ihre gesamte Umgebung zu bewegen – oftmals unbemerkt. Tenable Identity Exposure verschafft Ihnen vollständigen Einblick in Ihre komplexe Active Directory-Umgebung, priorisiert die größten Risiken für Ihr Unternehmen und unterstützt Sie bei deren Behebung, um Angriffspfade proaktiv zu beseitigen, bevor Angreifer sie ausnutzen können.
Kostenlos testen Mehr erfahrenAbsicherung Ihrer gesamten externen Angriffsoberfläche
Je mehr Assets, Services und Anwendungen mit Internetzugang Ihr Unternehmen einsetzt, desto größer wird Ihr Cyberrisiko, und oftmals bestehen blinde Flecken, von deren Existenz niemand Kenntnis hat. Dadurch wird Ihre externe Angriffsoberfläche zu einer Ihrer größten Bedrohungen. Tenable Attack Surface Management bildet das gesamte Internet kontinuierlich ab und erfasst Verbindungen zu Ihren internetfähigen Assets, damit Sie Ihre externen Risiken minimieren können.
Kostenlos testen Mehr erfahrenSchwachstellen schnell und präzise aufspüren und beheben
Ihre Schwachstellen zu kennen, ist eine Grundvoraussetzung für das Exposure-Management, und Nessus, der Goldstandard in Sachen Schwachstellenbewertung, ist das Herzstück von Tenable One. Zehntausende von Unternehmen weltweit vertrauen auf Nessus für die Analyse ihrer modernen Angriffsoberflächen. Die Lösung liefert ein präzises Bild, dass Ihnen hilft, Ihre Arbeit schnell und effektiv zu erledigen.
Kostenlos testen Mehr erfahrenMehr als 40.000 Kunden weltweit vertrauen auf unsere Lösungen.
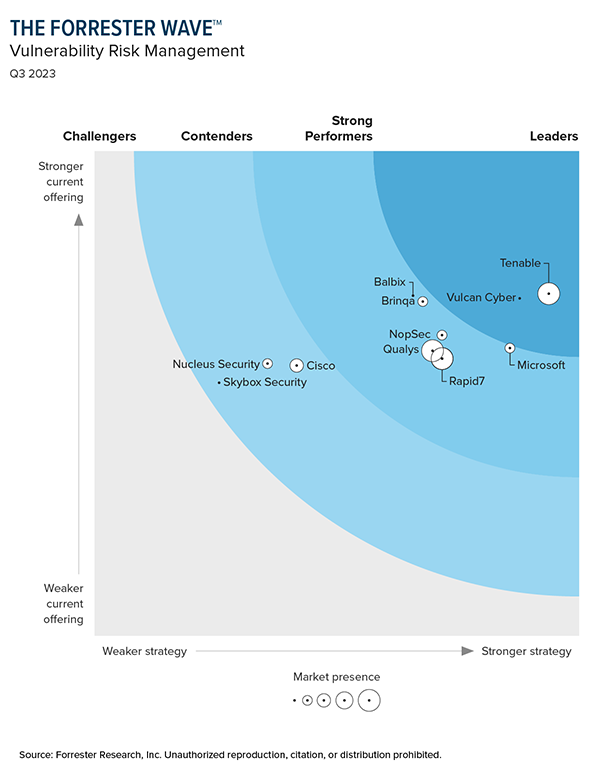
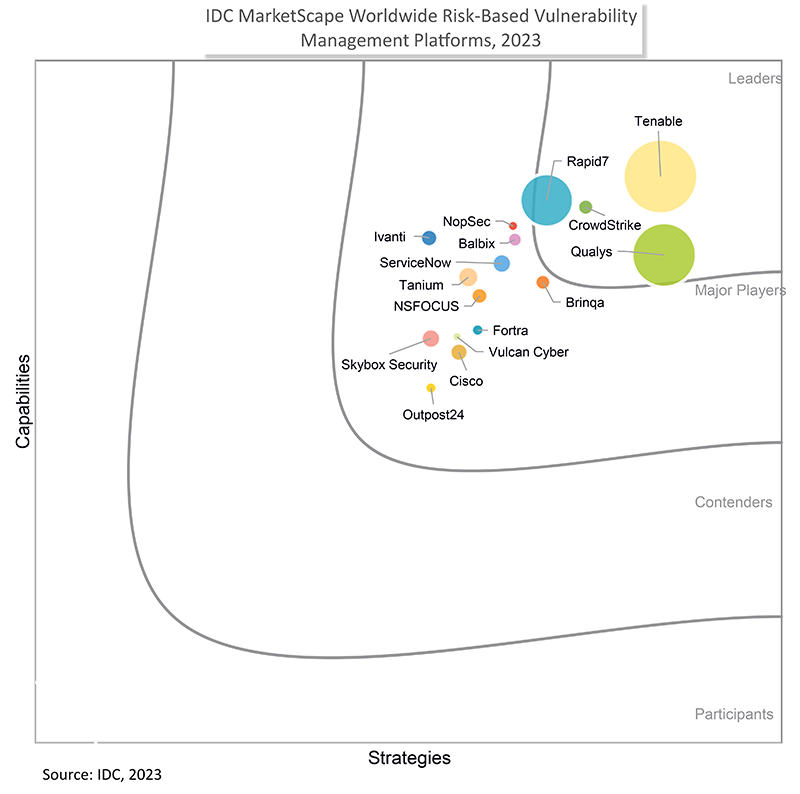
Anerkannt als ein Branchenführer
SC Awards 2023
Tenable One erhielt die Auszeichnung als „Best Risk/Policy Management Solution of the Year“
IDC: Nr.1 bei Device Vulnerability Management
Tenable belegt das fünfte Jahr in Folge den ersten Platz beim Marktanteil.
Behalten Sie Ihre dynamische Bedrohungslandschaft im Griff und seien Sie Angreifern stets einen Schritt voraus
Informieren Sie sich über CVEs (Common Vulnerabilities and Exposures) und beziehen Sie Bedrohungsdaten, datenwissenschaftliche Erkenntnisse, Warnungen und Sicherheitshinweise von der größten Einrichtung für Schwachstellenforschung in der Branche: Tenable Research.
Erkunden Sie die neuesten Forschungsergebnisseüber 174.000 Plugins bewertet
Januar 2019 aufgedeckt
von High-Profile-Problemen
Erleben Sie Tenable in Aktion
Möchten Sie erfahren, wie Tenable Ihrem Sicherheitsteam helfen kann, komplexe Cybersecurity-Herausforderungen schnell und präzise zu bewältigen? Füllen Sie dieses Formular aus, um weitere Informationen zu erhalten.
„Bei uns wird alles gründlich recherchiert. Die Entscheidung für Tenable lag auf der Hand.“Tenable Vulnerability Management
Wir bieten Ihnen vollen Zugriff auf eine moderne, cloudbasierte Schwachstellenmanagement-Plattform, mit der Sie alle Ihre Assets mit beispielloser Genauigkeit sehen und nachverfolgen können.
Ihre Testversion von Tenable Vulnerability Management umfasst außerdem Tenable Lumin und Tenable Web App Scanning.
Tenable Vulnerability Management
Wir bieten Ihnen vollen Zugriff auf eine moderne, cloudbasierte Schwachstellenmanagement-Plattform, mit der Sie alle Ihre Assets mit beispielloser Genauigkeit sehen und nachverfolgen können. Erwerben Sie noch heute Ihre jährliche Subscription.
Wählen Sie Ihre Subscription-Option:
Tenable Vulnerability Management
Wir bieten Ihnen vollen Zugriff auf eine moderne, cloudbasierte Schwachstellenmanagement-Plattform, mit der Sie alle Ihre Assets mit beispielloser Genauigkeit sehen und nachverfolgen können.
Ihre Testversion von Tenable Vulnerability Management umfasst außerdem Tenable Lumin und Tenable Web App Scanning.
Tenable Vulnerability Management
Wir bieten Ihnen vollen Zugriff auf eine moderne, cloudbasierte Schwachstellenmanagement-Plattform, mit der Sie alle Ihre Assets mit beispielloser Genauigkeit sehen und nachverfolgen können. Erwerben Sie noch heute Ihre jährliche Subscription.
Wählen Sie Ihre Subscription-Option:
Tenable Vulnerability Management
Wir bieten Ihnen vollen Zugriff auf eine moderne, cloudbasierte Schwachstellenmanagement-Plattform, mit der Sie alle Ihre Assets mit beispielloser Genauigkeit sehen und nachverfolgen können.
Ihre Testversion von Tenable Vulnerability Management umfasst außerdem Tenable Lumin und Tenable Web App Scanning.
Tenable Vulnerability Management
Wir bieten Ihnen vollen Zugriff auf eine moderne, cloudbasierte Schwachstellenmanagement-Plattform, mit der Sie alle Ihre Assets mit beispielloser Genauigkeit sehen und nachverfolgen können. Erwerben Sie noch heute Ihre jährliche Subscription.
Wählen Sie Ihre Subscription-Option:
Tenable Web App Scanning testen
Profitieren Sie im Rahmen der Exposure-Management-Plattform Tenable One von unserem neuesten Angebot zum Scannen von Webanwendungen, das speziell für moderne Anwendungen entwickelt wurde. Scannen Sie auf sichere Weise Ihr gesamtes Online-Portfolio auf Schwachstellen – mit hoher Genauigkeit und ohne großen manuellen Aufwand oder Unterbrechung kritischer Web-Apps. Melden Sie sich jetzt an.
Ihre Testversion von Tenable Web App Scanning umfasst außerdem Tenable Vulnerability Management und Tenable Lumin.
Tenable Web App Scanning kaufen
Wir bieten Ihnen vollen Zugriff auf eine moderne, cloudbasierte Schwachstellenmanagement-Plattform, mit der Sie alle Ihre Assets mit beispielloser Genauigkeit sehen und nachverfolgen können. Erwerben Sie noch heute Ihre jährliche Subscription.
3.578,00 USD
Tenable Lumin testen
Mit Tenable Lumin können Sie Ihr Exposure-Management visualisieren und genauer untersuchen, die Risikoreduzierung im Zeitverlauf verfolgen und Benchmark-Vergleiche mit ähnlichen Unternehmen anstellen.
Ihre Testversion von Tenable Lumin umfasst außerdem Tenable Vulnerability Management und Tenable Web App Scanning.
Tenable Lumin kaufen
Kontaktieren Sie einen Vertriebsmitarbeiter, um zu erfahren, wie Tenable Lumin Sie dabei unterstützen kann, unternehmensweit Einblick zu gewinnen und Cyberrisiken zu managen.
Demo von Tenable Security Center anfordern
Bitte tragen Sie Ihre Kontaktdaten in dieses Formular ein.
Ein Vertriebsmitarbeiter wird Sie in Kürze kontaktieren, um einen Termin für die Demo zu vereinbaren.
* Feld muss ausgefüllt werden
Demo von Tenable OT Security anfordern
Passgenauer Schutz Ihrer operativen Technologien –
durch effektive Risikoreduzierung.
Demo von Tenable Identity Exposure anfordern
Erkennung und Abwehr von Active Directory-Angriffen in Echtzeit. Keine Agents. Keine Zugriffsrechte.
On-Prem und in der Cloud.
Demo von Tenable Cloud Security anfordern
Außergewöhnliche, einheitliche Cloud-Sicherheit erwartet Sie!
Wir zeigen Ihnen genau, wie Tenable Cloud Security Ihnen hilft, Multi-Cloud-Assets zu erfassen, priorisierte Risikobewertungen vorzunehmen und automatische Compliance-/Audit-Berichte zu erstellen.
Erleben Sie
Tenable One
in Aktion
Exposure-Management für die moderne Angriffsoberfläche.
Erleben Sie Tenable Attack Surface Management in Aktion
Die Cyber Exposure sämtlicher Assets auf jeder Plattform jederzeit im Blick.
Testen Sie Tenable Nessus Professional kostenlos
7 TAGE KOSTENLOSTenable Nessus ist derzeit der umfassendste Schwachstellen-Scanner auf dem Markt.
NEU - Tenable Nessus Expert
Jetzt verfügbar
Nessus Expert bietet noch mehr Funktionen, darunter das Scannen externer Angriffsoberflächen sowie die Möglichkeit, Domänen hinzuzufügen und die Cloud-Infrastruktur zu scannen. Klicken Sie hier, um Nessus Expert zu testen.
Füllen Sie das Formular unten aus, um mit einer Nessus Pro-Testversion fortzufahren.
Tenable Nessus Professional kaufen
Tenable Nessus ist derzeit der umfassendste Schwachstellen-Scanner auf dem Markt. Tenable Nessus Professional unterstützt Sie bei der Automatisierung des Scan-Prozesses, spart Zeit in Ihren Compliance-Zyklen und ermöglicht Ihnen die Einbindung Ihres IT-Teams.
Mehrjahreslizenz kaufen und sparen! Mit Advanced Support erhalten Sie rund um die Uhr, 365 Tage im Jahr Zugang zum Support – per Telefon, Chat und über die Community.
Testen Sie Tenable Nessus Expert kostenlos
7 TAGE KOSTENLOSMit Nessus Expert, das für die moderne Angriffsoberfläche entwickelt wurde, erhalten Sie mehr Einblick und können Ihr Unternehmen vor Schwachstellen schützen – von der IT bis zur Cloud.
Sie haben Tenable Nessus Professional bereits?
Upgraden Sie auf Nessus Expert – 7 Tage kostenlos.
Tenable Nessus Expert kaufen
Mit Nessus Expert, das für die moderne Angriffsoberfläche entwickelt wurde, erhalten Sie mehr Einblick und können Ihr Unternehmen vor Schwachstellen schützen – von der IT bis zur Cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable-Lösungen unterstützen die Erfüllung aller SLCGP-Anforderungen. Kontaktieren Sie einen Vertriebsmitarbeiter von Tenable, um mehr zu erfahren.
Vielen Dank.
Sie sollten in Kürze eine Bestätigungs-E-Mail erhalten und einer unserer Sales Development-Mitarbeiter wird sich mit Ihnen in Verbindung setzen. Leiten Sie alle Fragen an [email protected] weiter.