In The Cloud and On-Prem, Threats Are Evolving
Proactively Identify and Address Cyber Risk
If your security team has limited cloud visibility, it can't answer, "How secure are we?". Tenable’s exposure management platform gives you visibility across your entire attack surface — with business context — so you can accurately understand your cyber risk and prioritize mitigation.

Extend Visibility. Prioritize Action. Communicate Risk.
You can’t secure your cloud if you can’t see all of your assets. From vulnerability management to cloud security, identity security to external attack surface management, and more — get the context you need to make more informed decisions based on your actual cyber risk.

Proactive Solutions for Common Cybersecurity Challenges
Cloud Security
Simplify Multi-Cloud Security and Entitlement Management
Rapid cloud adoption means you’re managing complex, multi-cloud environments. Yet, you may not have insight into everything in the cloud. With Tenable Cloud Security’s full asset discovery, deep risk analysis, runtime threat detection, and compliance support, you can reduce cloud complexity, minimize your cyber risk and enforce least privilege at scale.
Request a Demo Learn MoreVulnerability Management
Get Risk-Based Vulnerability Prioritization
Today’s IT landscape is so complex and rapidly changing, it can feel impossible to decipher which vulnerabilities pose an actual threat to your organization. And, if you’re still using legacy vulnerability management tools, you’ll never keep pace. Tenable Vulnerability Management enables real-time continuous assessment of your attack surface, giving you a risk-based, research-backed perspective about all of your vulnerabilities so you know which to fix first — including best practice recommendations to get you there.
Try for Free Learn MoreOperational Technology Security
Extend Visibility Across IT and OT Environments
As digital transformation accelerates, integrated IT and OT environments introduce an increased attack surface and blind spots. Without comprehensive visibility into all of your systems and assets, cyberattacks can easily propagate across your enterprise. Tenable OT Security provides complete visibility, unified security and prioritized threat management to mitigate risk.
Request a Demo Learn MoreActive Directory Security
Harden Active Directory and Eliminate Attack Paths in Your Environment
Behind almost every breach headline is an attack on Active Directory (AD). AD misconfigurations and other security issues allow attackers to gain access, elevate privileges and move laterally across your entire environment — often undetected. Tenable Identity Exposure enables you to see everything in your complex Active Directory environment, prioritizes the greatest risks to your organization, and helps with remediation to proactively eliminate attack paths before attackers can exploit them.
Try for Free Learn MoreExternal Attack Surface Management
Secure Your Entire External Attack Surface
As your organization adopts more internet-exposed assets, services and apps, your cyber risk increases, often with blind spots no one knows are there. This makes your external attack surface one of your greatest threats. Tenable Attack Surface Management continuously maps the entire internet and discovers connections to your internet-facing assets so you can mitigate your external risks.
Try for Free Learn MoreVulnerability Assessment
Find and Fix Vulnerabilities Fast and Accurately
Understanding your vulnerabilities is foundational to exposure management, and Nessus, the gold standard in vulnerability assessment, is at the core of Tenable One. Trusted by tens of thousands organizations worldwide to assess their modern attack surfaces, Nessus provides an accurate picture to help you do your work quickly and effectively.
Try for Free Learn MoreSimplify Multi-Cloud Security and Entitlement Management
Rapid cloud adoption means you’re managing complex, multi-cloud environments. Yet, you may not have insight into everything in the cloud. With Tenable Cloud Security’s full asset discovery, deep risk analysis, runtime threat detection, and compliance support, you can reduce cloud complexity, minimize your cyber risk and enforce least privilege at scale.
Request a Demo Learn MoreGet Risk-Based Vulnerability Prioritization
Today’s IT landscape is so complex and rapidly changing, it can feel impossible to decipher which vulnerabilities pose an actual threat to your organization. And, if you’re still using legacy vulnerability management tools, you’ll never keep pace. Tenable Vulnerability Management enables real-time continuous assessment of your attack surface, giving you a risk-based, research-backed perspective about all of your vulnerabilities so you know which to fix first — including best practice recommendations to get you there.
Try for Free Learn MoreExtend Visibility Across IT and OT Environments
As digital transformation accelerates, integrated IT and OT environments introduce an increased attack surface and blind spots. Without comprehensive visibility into all of your systems and assets, cyberattacks can easily propagate across your enterprise. Tenable OT Security provides complete visibility, unified security and prioritized threat management to mitigate risk.
Request a Demo Learn MoreHarden Active Directory and Eliminate Attack Paths in Your Environment
Behind almost every breach headline is an attack on Active Directory (AD). AD misconfigurations and other security issues allow attackers to gain access, elevate privileges and move laterally across your entire environment — often undetected. Tenable Identity Exposure enables you to see everything in your complex Active Directory environment, prioritizes the greatest risks to your organization, and helps with remediation to proactively eliminate attack paths before attackers can exploit them.
Try for Free Learn MoreSecure Your Entire External Attack Surface
As your organization adopts more internet-exposed assets, services and apps, your cyber risk increases, often with blind spots no one knows are there. This makes your external attack surface one of your greatest threats. Tenable Attack Surface Management continuously maps the entire internet and discovers connections to your internet-facing assets so you can mitigate your external risks.
Try for Free Learn MoreFind and Fix Vulnerabilities Fast and Accurately
Understanding your vulnerabilities is foundational to exposure management, and Nessus, the gold standard in vulnerability assessment, is at the core of Tenable One. Trusted by tens of thousands organizations worldwide to assess their modern attack surfaces, Nessus provides an accurate picture to help you do your work quickly and effectively.
Try for Free Learn MoreTrusted by More Than 40,000 Customers
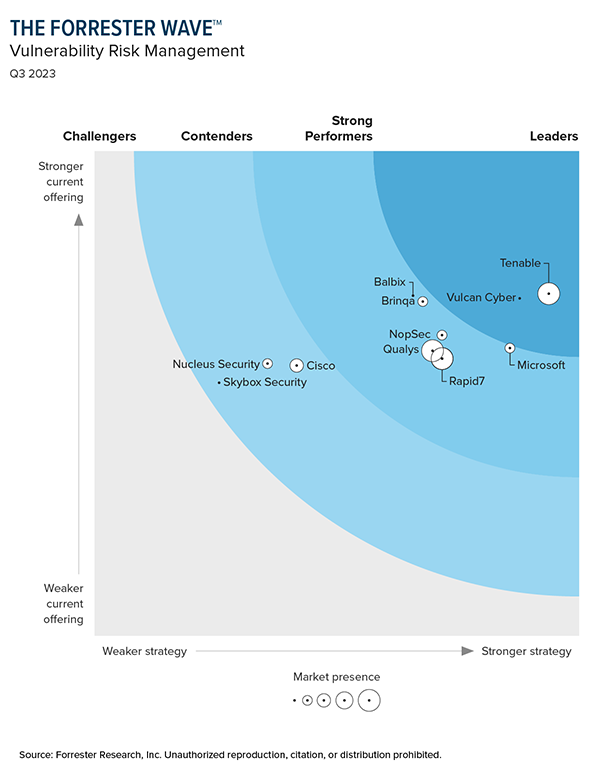
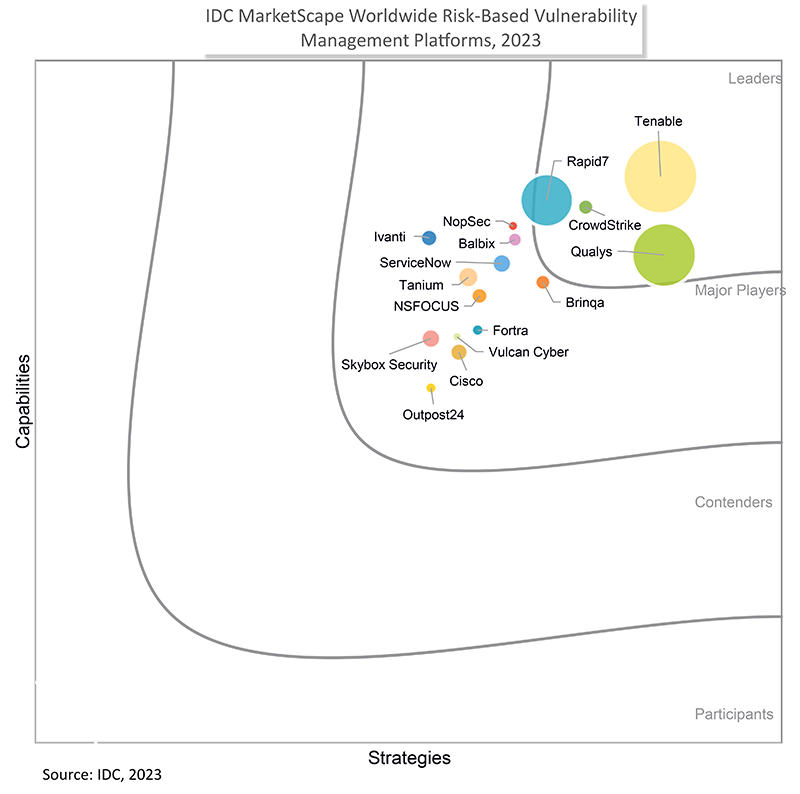
Recognized as an Industry Leader
IDC: #1 in Device Vulnerability Management
For the fifth consecutive year, Tenable ranks No.1 in market share
Stay on Top of Your Fast-moving
Threat Landscape and Get Ahead of Attackers
Review common vulnerabilities and exposures (CVEs), get threat intelligence, data science insights, alerts and security advisories from the largest vulnerability research organization in the industry — Tenable Research.
Explore the Latest Researchwith 174,000+ plugins
since January 2019
of high profile issues
See Tenable in Action
Want to see how Tenable can help your security team quickly and accurately overcome complex cybersecurity challenges? Complete this form for more information.
"We do in-depth research on everything. Tenable came out as the clear choice.”Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Choose Your Subscription Option:
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Choose Your Subscription Option:
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Choose Your Subscription Option:
Try Tenable Web App Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
$3,578
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Request a demo of Tenable Security Center
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Continuously detect and respond to Active Directory attacks. No agents. No
privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Know the exposure of every asset on any platform.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYSTenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYSBuilt for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
Thank you.
You should receive a confirmation email shortly and one of our Sales Development Representatives will be in touch. Route any questions to [email protected].