Threat Hunting 202: Practical Whitelisting

In my last blog, I talked about DNS and its importance as an indicator of malicious activity. Once you’re past the quick wins stage, what’s the next step? Most of the difficulty with threat hunting is the overwhelming quantity of data. Once you’re monitoring everything needed to recreate attacks, it quickly becomes more than you can work with effectively.
One of the most important things that you can do to tune out the noise is to leverage whitelisting within your monitoring system for known-good or known-normal activities. The events will all still be there when you need them, but you won’t be alerted on them.
Most of the difficulty with threat hunting is the overwhelming quantity of data
Analytics and whitelisting
You can leverage the segmentation discussed in my previous blog post to build a profile of normal DNS activity for a server environment or for other devices that have known behaviors. This gives you rapid insight into any abnormal requests coming from these environments.
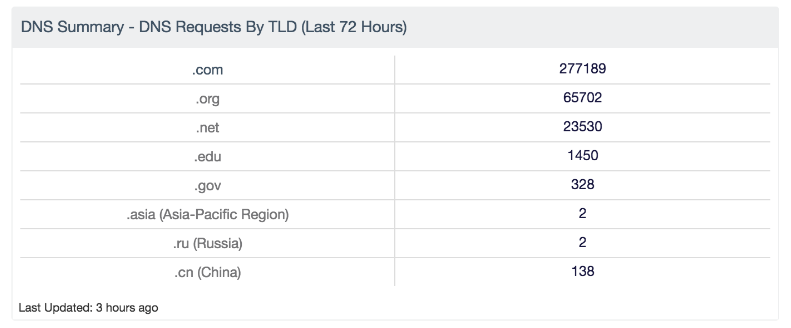
Start with a summarized view of traffic in your environment like the DNS Summary dashboard for SecurityCenter Continuous View™ (SecurityCenter CV™). I’m going to walk you through how I tuned this data for effective monitoring in one of our environments, so you can apply the same techniques to yours.
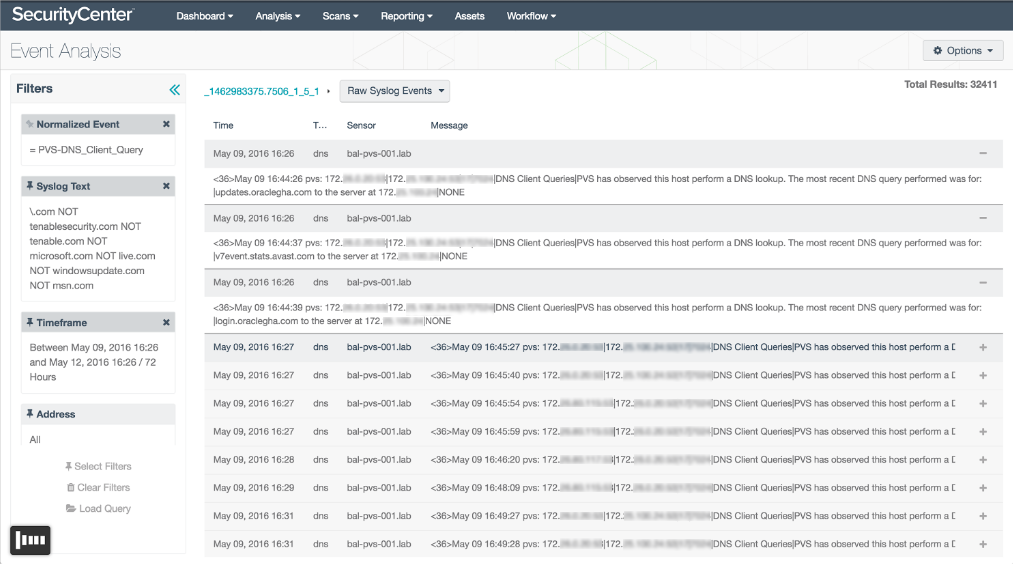
This is a lab environment, so there are some immediate things to check out. Top-level domains (TLDs) for non-US countries are always suspicious unless they serve a known business purpose. That’s a great quick win. Additional suffixes can be added to the summary element for monitoring to meet your business needs; this is just a default set.
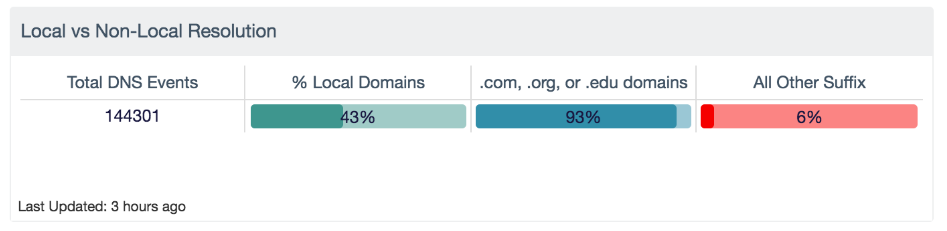
Looking at overall traffic, you can build a quick custom overview for how much DNS is happening to internal domains, external common domains, and any other activity out there:
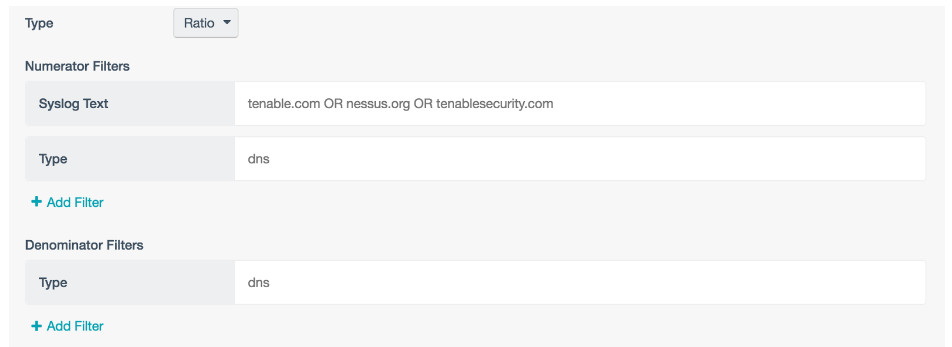
To build this, you can use a matrix element with a ratio of events. You are matching local known domains against the entirety of the DNS event set:
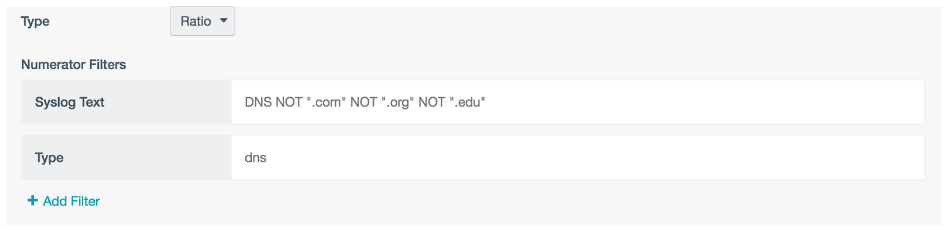
To pull the “All Others” information, you can use negative filtering in the same ratio element:
These are examples of filters you can create to quickly see what’s going on in your environment.
Since .com is the most used TLD in this lab traffic, the next step is walking through an example of profiling it, and then creating alerts for deviations. As you create these, you will get false positives, but once they’re in place and working, they’re great warning indicators. I would not recommend this process for more dynamic user environments and workstations. Leverage the environments that have regular patterns of activity that you can profile.
Drilling into the .com events, you can exclude known corporate domains and jump into the raw event view. Click into the first few, and see if the domains are known to be good. In this example, there are Microsoft domains, and some update URLs for vendor products, and Google. With each iteration of filtering domains, the number drops significantly, so you know you are moving in the right direction.
As the numbers drop, misconfigurations in your environment will surface: misspelled domains, or processes calling to example.com and other unconfigured vendor defaults in applications. These are also quick wins for security to work through with server administrators to reduce the number of false positives in your environment. Each resolved issue is another step toward improving the effectiveness of your security monitoring and reducing your false positive rate.
What we’re doing is whitelisting domains at the most basic level. At the end of the process, you’ll end up with a list of the most commonly accessed domains in the environment you’re working with, you’ll be able to set up alerts to summarize any activity you haven’t caught, and provide a warning of abnormal activity.
To configure alerts, save your search as a query and leverage it using the process discussed in Threat Hunting 101.
For more information about threat hunting with Tenable, check out these resources:
- [Video] Threat Hunting Demo with SecurityCenter Continuous View
- Finding Threats on Your Network: Hunt or Be Hunted
- Making CDM Work For You with Threat Hunting
- Have You Been Compromised? Let’s Go Hunting!
- Are You Ready to Go Hunting for Threats?
- Threat Hunting 201: Quick Wins with DNS
Stay in touch with Tenable. Subscribe to the Tenable Blog by clicking Blog email updates on the Blog Home Page.
Related Articles
- SecurityCenter
- Threat hunting