Securing Industrial Control Systems Against Vulnerabilities and Malware

Recently, a new threat dubbed Industroyer or CrashOverride was identified as the malware that was used in the 2016 attack on the Ukraine electric grid. Many pros are calling Industroyer the biggest threat to hit industrial control systems (ICS) since Stuxnet. However, Industroyer’s significance as a single event is relatively small because there are no zero days in the Industroyer payload.
Malware like Industroyer is the new normal
Security for critical infrastructure is a matter of national security and unfortunately, malware like Industroyer is the new normal. Multiple smaller attacks could easily add up to a disruptive event. Instead of reacting to every new malware threat, administrators should take a long-term strategic approach to this new environment.
Complying with a good security framework is one of the most effective security strategies you can adopt instead of just reacting to newsworthy vulnerabilities
ICS/SCADA systems often cannot be scanned or patched due to uptime requirements or simply because legacy systems have no means of being updated. So, when Industroyer was announced, the North American Electric Reliability Corporation (NERC) issued an alert to their members to be vigilant and to protect their networks with tighter access controls. They recommend their NERC Critical Infrastructure Protection Standards as best practice requirements for utilities to secure their assets. Complying with a good security framework takes time, but it is one of the most effective security strategies you can adopt instead of just reacting to newsworthy vulnerabilities.
How Industroyer works
Industroyer employs a modular design, and can be broken down into four basic components:
- Backdoor - sets up a command and control channel over https once the system is infected
- Launcher - launches one or more payloads
- Four payloads - one payload for each SCADA protocol that Industroyer supports:
- IEC 60870-5-104
- IEC 60870-5-101
- IEC 61850
- OLE for Process Control Data Access (OPC)
- Data wiper - a component that wipes itself from the system
There is an additional backdoor which could be installed to maintain persistent control over the system by replacing a legitimate version of Notepad with a trojanized version of Notepad.
The malware authors also released a tool which performs a DoS attack against the Siemens SIPROTEC family of protection relays.
Tenable solutions that detect SCADA protocols
Tenable offers several solutions to detect the the ICS/SCADA protocols targeted by Industroyer and other malware.
Nessus
YARA signatures are available to detect one or more of the Industroyer/CrashOverride payload components. Tenable customers can use YARA rules to identify infected systems with the Malicious File Detection Using Yara Nessus® plugin.
You’ll find sample rules that can be used with Nessus to detect the IOCs on GitHub.
Nessus Network Monitor
Nessus® Network Monitor (formerly PVS™) has released signatures to detect a DoS attack on the Siemens SIPROTEC family of protection relays (SIPROTEC DoS, CSA-15-202-01/ CVE-2015-5374): PRM #700132, Siemens SIPROTEC DoS (SCADA).
Using SecurityCenter dashboards for strategic protection
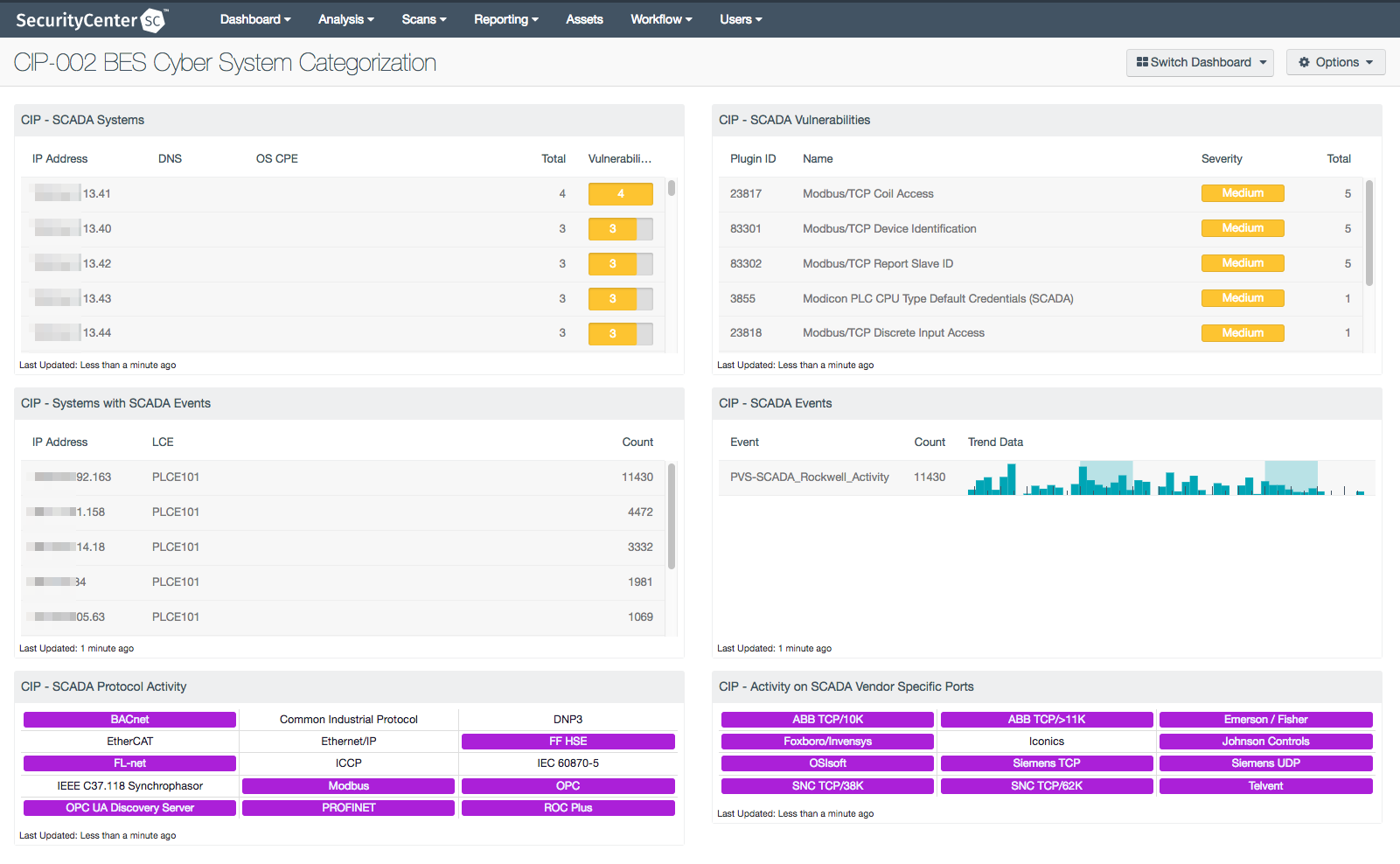
Using the Nessus vulnerability scanner and Nessus Network Monitor, SecurityCenter Continuous View® (CV) has the ability to correlate collected data and provide insight into the discovered risks. SecurityCenter® can help administrators focus in on a new critical vulnerability (such as Industroyer/CrashOverride) when it is detected in their networks. But ICS/SCADA systems require more than a periodic scan for the latest vulnerability; a complete discovery inventory, passive and active monitoring, and credentialed scans should be included as best practices. In the NERC Critical Infrastructure Protection Standards, the first strategic steps are to inventory the systems on the network, and ensure all protocols in use on the networks are properly identified. The CIP-002 BES Cyber System Categorization dashboard assists with host discovery and vulnerability identification, helping you get a broader picture of your network security.
CIP-002 requires organizations to identify and categorize Bulk Electric System (BES) Cyber Systems to support appropriate protection against compromises that could lead to misoperation or instability in the BES. You can meet this requirement by building and maintaining an accurate inventory of devices so that any attack or infection can be effectively detected and isolated. Additionally, once you know what devices are part of your NERC environment, you will be prepared to address CIP-007 R1 by monitoring network traffic to detect ports or services that should not be in use.
CIP-007 R1 requires organizations to protect against the use of unnecessary physical input/output ports used for network connectivity, console commands, or removable media. If unauthorized traffic is detected, the accurate inventory you built will be key in identifying and addressing the devices involved. The CIP-007 R1 Ports and Services dashboard provides thorough insight into the network activity in your organization by monitoring open ports and active services. The dashboard also identifies the usage SCADA-specific protocols as well as protocols from SCADA vendors. Since targeted malware, like Industroyer/CrashOverride, can exploit SCADA protocols to compromise BES systems, understanding the expected and acceptable traffic within your NERC environment is essential. The network activity detections are performed by the Tenable Nessus Network Monitor, and other network traffic collected by the Tenable Log Correlation Engine® (LCE®) are normalized and correlated to identify traffic patterns and anomalies. Active scan data from SecurityCenter is used in this dashboard to detect vulnerable ports and exploitable services. All of the data helps you resolve misused or misconfigured ports and services to protect your network against malicious activity.
There are six other dashboards related to CIP available in the SecurityCenter Feed:
- CIP-004 R4/R5 Access Management, Revocation, and Control
- CIP-005 Electronic Security Perimeter
- CIP-007 R3 Malicious Code Prevention
- CIP-010 R1/R2 Configuration Change Management and Monitoring
- CIP-010 R3 Vulnerability Assessment and Patch Management
- CIP-010 R4 Transient Cyber Assets and Removable Media
These dashboards can help you monitor a variety of other network security concerns, such as access control and change management. Other dashboards monitor for vulnerabilities and malware in your NERC environment. You can also track transient devices and monitor your network perimeter with CIP dashboards, giving you a complete view of network access and usage. This set of dashboards leverages active and agent scan data gathered by Nessus, along with passive network detections by the Nessus Network Monitor and correlated event data from LCE. Armed with all of this information about your NERC environment, you will be prepared to remediate issues and maintain CIP compliance. Determining whether your environment is vulnerable to malware in the news that day is important, but a strategic and thorough approach aided by SecurityCenter CV prepares you to ensure the security of your network when the hype fades.
Wrap-up
The key to managing a great security program is being strategic rather than tactical
Don’t fall into the trap of chasing down the latest headline-making vulnerability on your SCADA systems. A unified platform like SecurityCenter provides a more strategic approach to securing industrial systems and critical infrastructure with active and passive monitoring of your systems. If your AV systems, patching programs, and signatures are kept up to date on a regular basis; if you run credentialed scans for misconfigurations; if you implement protocols to assure that only the appropriate devices are communicating with each other; if you audit CIP compliance, then the next malware crisis will not be a major threat to your environment. The key to managing a great security program is being strategic rather than tactical.
Many thanks to Megan Daudelin, Ian Parker and John Chirhart for their contributions to this blog.
Related Articles
- Energy Industry
- Malware
- Nessus Network Monitor
- SCADA
- Security Policy
- Center for Internet Security (CIS)
- Standards
- Threat Management
- Vulnerability Management
- Vulnerability Scanning