Knowledge is Power: Computer Forensics to Detect and Respond to Breaches
High profile security breaches continue to occur (see infographic) in spite of the large investments that companies are making to secure their businesses and IT infrastructures. According to Mandiant’s 2014 Threat Report, two-thirds of the companies that have been breached did not find out about it until it was reported in the media. And the cyberattackers were present on the network for approximately 32 weeks before they were detected by the company. Security breaches have become a board level concern; every company that relies on IT infrastructure to do business is susceptible to a cyberattack – it is not a matter of if, but when!
Ask yourself this question: is your company’s security operations staff prepared to address security breaches before you discover that your business critical systems have been hacked? Effective and rapid incident response processes should be in place and endorsed by the entire organization, for any business to assess the business impact associated with cyberattacks.
Challenges with identifying and responding to security breaches
In a recent report from the consulting firm KPMG, the main reasons that companies are failing to perform successful incident response (IR) can be summarized as:
- People/Skills: IR teams often lack authority, management oversight and visibility across the entire organization.
- Process: IR processes and procedures are not well defined, and teams are not trained on the proper ways to identify and respond to breaches.
- Technology: IR tools are inadequate, unmanaged, untested, underutilized, unmanaged or absent. And data that is pertinent to an incident is often not readily available.
Actionable forensic data to identify compromised systems
Forensic tools must be available to detect compromises and diversions from the norm so that an effective and rapid response can be implemented
The incident response team must have tools in place to assess the integrity of a company’s systems. First, a baseline must be established to understand normalcy. And second, forensic tools must be available to detect compromises and diversions from the norm so that an effective and rapid response can be implemented. Forensic data includes:
- Network Forensics: Logs of all network traffic, which includes packet metadata from network sensors, application flow data from switches and routers, and application logs from network proxies. This data is useful for identifying suspicious traffic that can be attributed to botnets or command and control (CnC) servers to or from bad sites without deploying any agents on endpoints.
- Host Forensics: Monitoring hosts and endpoints for file integrity, system configurations, processes, DNS queries, and network connections. This typically requires credential based scanning of endpoints, or agents running on endpoints to gather evidence (using telltale signs of indicators of compromise).
- Log Correlation: Encompasses behavioral and statistical analysis to determine anomalies in network and host forensic data. Infuses contextual information about asset location and user identity, and also filters logs using blacklists from external threat intelligence sources. These correlation features are vital for zeroing in on security incidents that need immediate attention.
Flexible incident response techniques
Any solution that identifies security events and incidents should further enable you to respond to them with configurable actions, based on the simplicity or complexity of the problem identified. Such responses may include:
- Notifications/Email: Sending notifications via the console or by email, and including the recommended action.
- Dashboards/Reports: Automatically updating a dashboard or generating a report with the current state of incidents in progress, assigned to the appropriate personnel.
- Work Flows: Triggering trouble tickets with workflows assigned to the person responsible for follow through. This response is especially useful for the most complex and the least understood incidents.
- Automated Actions: Automatically invoking scripts or application programmatic interfaces (APIs), which perform specific actions such as adding a URL to the blacklist of a web gateway or updating an ACL on a firewall to automatically block CnC servers. Automated actions are most applicable for frequently occurring incidents that are well understood.
Tenable’s continuous network monitoring solution
Tenable’s SecurityCenter Continuous View™ (SecurityCenter CV™) solution enables the capture of actionable forensic data and provides configurable alerts to detect and respond to security breaches in real time.
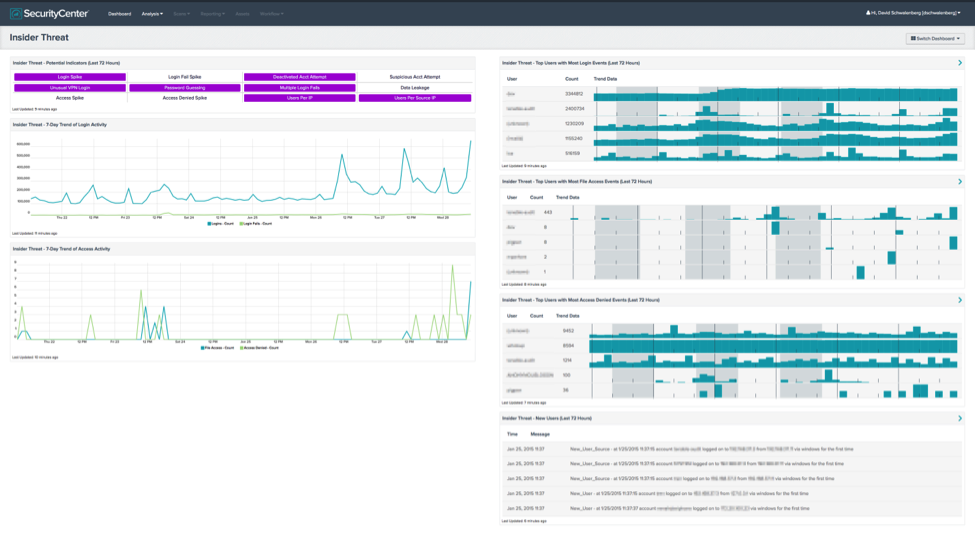
SecurityCenter CV can be used to track both inbound and outbound suspicious network traffic and collect host and network level forensic data related to attacks. Numerous dashboards in the SecurityCenter feed provide tools for forensics analysis. For example, the Insider Threat Dashboard reports information about user logins and resource access activity. The dashboard displays indicators that can help an analyst track down authorizations and detect a potential inside attacker.
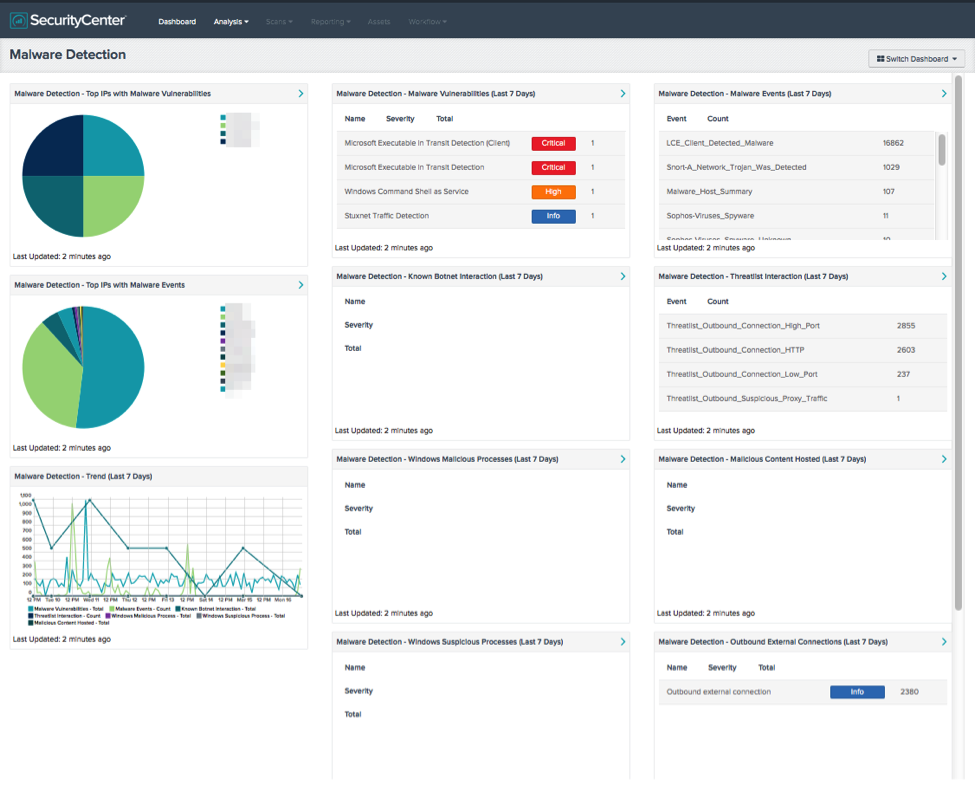
In addition, SecurityCenter CV can identify endpoints compromised by advanced malware, by scanning for indicators of compromise using threat intelligence built into it:
Finally, SecurityCenter CV Helps security managers respond to events and incidents by setting up configurable response actions (alerts/notifications/workflows).
More resources
Consult the following resources to learn more about how SecurityCenter CV provides forensic data and meets the challenges of incident response:
- Speed Up Incident Response with Actionable Forensic Analytics – Paper about forensics, incident response and SecurityCenter CV
- Accelerate Incident Response with Actionable Forensic Analytics – Recorded webcast about forensics and incident response
Related Articles
- SecurityCenter
- Threat Management
- Vulnerability Management