IT is from Mercury, ICS is from Mars

Although both are technical and vital in their own right, when it comes to people, processes and technology, Information Technology (IT) has little in common with Industrial Control Systems (ICS). Borrowing from best-selling author John Gray, it is as if IT is from Mercury (1 Mercury year = 88 earth days), and ICS is from Mars (1 Mars year = 687 earth days). When technologies and processes from the two planets converge, the result can be a time warp that disorients people from both worlds.
ICS is running critical infrastructure
On Mercury, IT staff members can afford to take calculated risks on non-mission critical systems because failures are often minor and correcting them may be as simple as rebooting a system. IT processes enable agility, and changes may be managed from start to finish in hours or days. The life expectancy for IT technology is typically three to five years.
Information Technology (IT) has little in common with Industrial Control Systems (ICS)
On the other hand, life on Mars moves noticeably slower. System failures can result in production outages that cost millions of dollars, as evidenced by “massive damage” at a steel mill in Germany. So on Mars, change management is often an arduous process—testing alone can require months of effort. Furthermore, the often proprietary industrial control systems may live for decades and require people with specialized skill sets to support them.
The SANS Institute offers timely insight
For a closer look at the state of ICS security and its relationship with IT, you should check out the SANS Institute’s upcoming June 25th webcast, The State of Security in Control Systems Today. The webcast will explore the results of a survey SANS conducted this spring. Tenable was one of the organizations co-sponsoring this research project.
The SANS study has broad applicability across multiple industries, such as automated manufacturing, pharma, water, oil, gas, energy and utilities. I was fortunate enough to receive a preview copy and found it was full of useful information covering:
- Security threats and drivers
- Security controls and methodologies
- IT–ICS convergence
- Security budgets
While the entire report is valuable, a controversial section about IT–ICS convergence caught my attention. Frameworks from the North American Reliability Corporation (NERC) and the Federal Energy Regulatory Commission direct IT and operational technology staffs working for organizations operating “critical infrastructure” to work together and manage risks cooperatively. It reminds me of my parents telling me and my sister to “get along.”
Certainly, IT and ICS technologies are converging
Certainly, IT and ICS technologies are converging. Commercial operating systems and standard networking protocols are finding their way into control system networks that were once dominated by proprietary operating systems and ICS specific protocols, such as Modbus and DNP3. The survey describes this as a “seismic shift.” And, like most seismic shifts, it will occur very slowly.
From a security perspective, there is great concern that active vulnerability scanning and configuration auditing will disturb ICS networks, cause crashes, and may result in expensive and even disastrous downtime. The report advises practitioners to use ICS specific tools, such as traffic monitoring applications, and that sounds good on the surface. However, I think a better solution is to use security tools that are common across IT and ICS whenever possible. This implies that the security tools include passive monitoring capabilities that won’t conflict with the reliable operation of ICS devices or with vendor certification requirements.
Converged security tools, assuming they are compatible with both IT and ICS technologies, would likely offer both cost of ownership reductions and technical advantages
Converged security tools, assuming they are compatible with both IT and ICS technologies, would likely offer both cost of ownership reductions and technical advantages. Cost of ownership reductions would accrue from having a single solution (albeit with potentially different instances—one for IT and one for ICS) to learn, manage and maintain. So, for example, a power user from ICS could help a less experienced user in IT customize a dashboard or a report to meet a specific requirement.
Additionally, if the ICS team needs help investigating and resolving a security issue on Windows or Linux based systems, they could enlist the expertise of the IT security staff. For example, if a Windows based system on the ICS network started reporting unusually high CPU usage, a Windows expert from IT may be able to help inspect the running processes and interpret the system’s logs to determine the root cause.
Bridging the IT–ICS divide
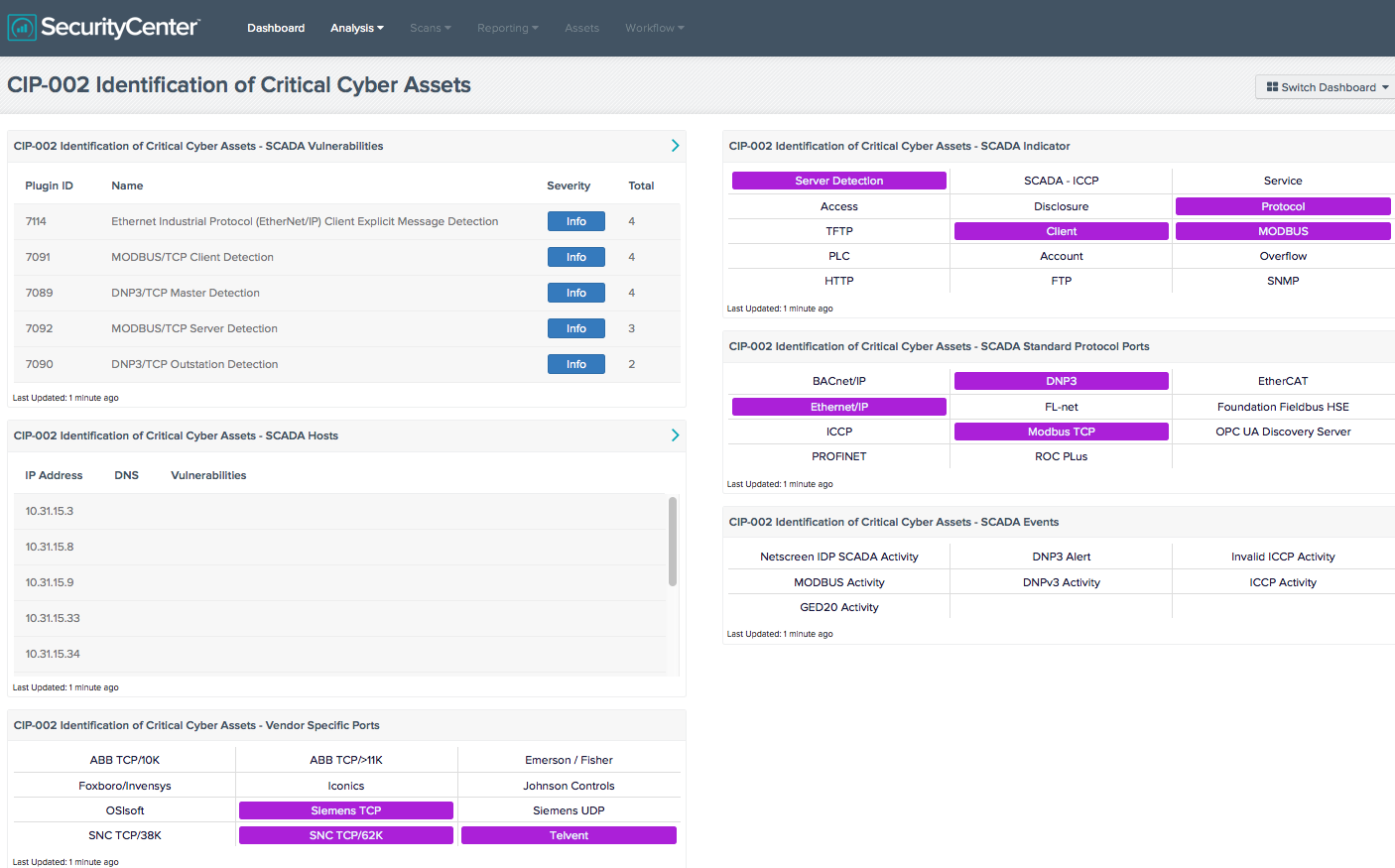
SecurityCenter Continuous View™ (SecurityCenter CV™), Tenable’s continuous network monitoring solution, is fluent in both “Mercurian-ese” and “Martian-ese” and can identify vulnerabilities, reduce risk and ensure compliance on both planets. Its passive network monitoring capability benignly analyzes network traffic—without generating any traffic—and can identify hundreds of different IT and ICS specific devices and protocols active on an ICS network. SecurityCenter CV also has the ability to detect ICS specific malware, such as StuxNet. SecurityCenter CV can alert users whenever a new device, protocol, port or connection becomes active. ICS networks are typically quite static, so detecting a new device or connection may indicate malicious activity. This screenshot shows how SecurityCenter CV addresses the CIP 002 Identification of Critical Cyber Assets control:
Additionally, SecurityCenter CV can monitor ICS networks and develop a statistical model of normal behavior on an hour-by-hour basis. For example, if a specific device normally sends 30 KB of data between 1 am and 2 am, SecurityCenter CV will create an event if the amount of data varies in a statistically significant way; and depending upon the severity, it can also issue an alert.
SecurityCenter CV assures network health on both planets, without requiring them to align or you to teleport between the two worlds.
Learn more
Please mark your calendar to join the SANS webcast at 1pm ET on June 25th. You may also find these Tenable whitepapers relevant:
Related Articles
- Announcements
- Conferences
- Events
- Research Reports
- SANS
- SCADA