Detecting Credit Cards, SSNs and other Sensitive Data at rest with Nessus
Note: This blog entry was originally posted in March, 2007 and was updated on May 28, 2009
Tenable Network Security has released a new Nessus plugin named "Windows File Contents Check" (plugin ID #24760). It is available in Nessus and has the ability to find a wide variety of sensitive data at rest on Windows computers. This blog entry describes how the checks work and how Nessus users can benefit from them. This new plugin is also supported in Security Center which is covered in a separate blog entry.
Why Find Sensitive Data?
Finding and identifying where your sensitive data is within an organization allows better prioritization of security issues and can find systems (and users) that are not authorized to possess that data.
When sensitive data is identified, an analyst can ask one of two questions:
- Is this data authorized to be on this server at all?
- Does the system that holds this data have proper access control, patch management and overall security?
When combined with Nessus' ability to find systems with vulnerabilities and systems that are not being managed, detecting sensitive data can focus an IT organization's efforts to remain compliant and reduce risk of data loss.
- Unauthorized systems and users with access to sensitive data can be detected and rectified.
- Authorized systems with sensitive data and vulnerabilities or mis-configurations can be given priority over similar systems that do not hold sensitive data.
What kind of Data is "Sensitive"?
Every organization has a wide variety of data that is important, but few organizations have built a data dictionary or a classification scheme.
Most readers are familiar with the government's use of the terms "SECRET" and "TOP SECRET". There have also been many cases of financial, academic and commercial institutions losing large volumes of customer credit card numbers, social security numbers, addresses and phone numbers.
Your organization most likely has its own list of things that it considers "intellectual property". Perhaps it is source code or a copy of a manuscript that has not been released.
This new Nessus check can help find many different types of this kind of data.
Here is an example screen shot of detecting a Social Security Number in an Excel spreadsheet on a remote Windows system:
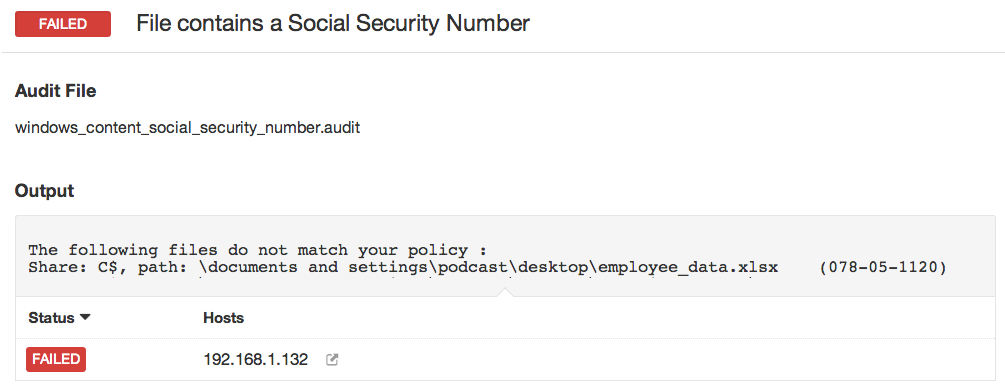
How does it work?
The current check supports credentialed scans of a Windows server. Like all Nessus credentialed scans, it does not require an agent but it does require an account that has login credentials and the ability to read the disk. A domain administrator account can be used to perform these checks.
Each scan is given one or more ".audit" files that have the same type of format and structure as Nessus's compliance checks. Here is a short example that looks for a Social Security Number:
<check_type:"WindowsFiles">
<item>
type: FILE_CONTENT_CHECK
description: "Determine if a file contains a SSN"
file_extension: "txt" | "doc" | "xls" | "pdf"
regex: "([^0-9-]|^)([0-9]{3}-[0-9]{2}-[0-9]{4})([^0-9-]|$)"
expect: "Social Security Number" | "SSN" | "SS#" | "Social"
max_size : "50K"
</item>
</check_type>When invoked, the remote Windows host will compute a list of all local files with extensions for text, Word, Excel and Adobe files. It will then send the first 50K bytes of each file to Nessus over a secure SMB link. All data obtained by the plugin will be searched for the data patterns in the .audit file. In the above case, any of the strings "Social Security Number", "SSN", "SS#" or "Social" are required to be present. The regular expression is used to look for at least one SSN.
If the system is scanned and no sensitive data is found, it is logged as a "PASS". Otherwise, it is logged as a FAILURE.
Other technical details include:
- Any file extension can be used.
- For PDF files, the Nessus plugin automatically decodes the PDF encoding.
- A regular expression statement is optional, however, the "expect" statement that contains basic string matches is always required.
- There is an additional keyword named "only_show" which only shows the last "n" bytes of a matched file.
Protecting the Auditors
Below is an example of a .audit policy to search for American Express credit card numbers:
<check_type:"WindowsFiles">
<item>
type: FILE_CONTENT_CHECK
description: "Determine if a file contains a valid American Express Card Number"
file_extension: "xls" | "pdf"
regex: "([^0-9-]|^)(3(4[0-9]{2}|7[0-9]{2})( |-|)[0-9]{6}( |-|)[0-9]{5})([^0-9-]|$)"
expect: "American Express" | "CCAX" | "amex" | "credit"
max_size : "50K"
only_show : "4"
</item>
</check_type>As an auditor, you might think it very interesting to start collecting credit cards, personal data and so on, but organizations that are trying to limit where this type of data goes do not want to compound the problem.
Rather than making your audit team part of your "sensitive" data controls, all of the audits performed by Nessus can limit the amount of data that is displayed. The "only_show" keyword in the audit file will display the last "N" bytes of data. For example if an example credit card of "1122-3344-5566-7788" was found, it would only display "XXXXXXXXXXXXXXX7788".
Obtaining and Running These Checks
Nessus ProfessionalFeed users on Red Hat, Solaris and OS X can simply update their plugins. Along with the new plugin, a new plugin preference named "Windows File Contents Compliance Checks" will be available. The new plugin will also be available under the "Policy Compliance Family".
To run a check, download a .audit file (or write your own), build a scanning policy that includes the new plugin and your .audit file and then perform a scan against a Windows host with the proper credentials.
Tenable is adding more and more example .audit files at the Tenable Support Portal. These files are listed alongside the configuration .audit files for NIST, NSA and CERT audit standards and many more. Currently, the Sensitive Content Audit Policies .audit files are offered for discovery of:
- Employee Identification Number
- Employee Salary List
- Financial Statement
- International Wire Transfer
- Non Disclosure Agreements
- Source Code Leakage
- Classified Documents
- EDI Claim Information
- Credit Card Number
- Driver’s License
- Social Security Number (Generic)
- Social Security Number (by State)
Optimizing These Checks
While BETA testing these .audit files, there were several trade-offs than any organization needs to consider:
- Which extensions should we search for?
- How much data must be scanned?
The .audit files do not require the "max_size" keyword. In this case, Nessus will attempt to retrieve the entire file and will continue until it has a match on a pattern. Since these files traverse the network, there is more network traffic with these audits than with typical scanning or configuration auditing.
Searching for more extensions may encounter unexpected results. For example, Trillion chat logs are saved as .txt files. If you have a user who placed an SSN or a credit card number in a chat session once, that may show up.
Searching for less data, such as just the first 5000 bytes is much faster than searching for the first 50K bytes, but is much less in depth.
For More Information
There is a separate blog entry that describes using this plugin in an enterprise network as part of a comprehensive vulnerability, configuration and sensitive data audit environment.
To purchase Nessus, visit the Tenable Store.
Related Articles
- Compliance Monitoring





