Canada’s Information Technology Security Guidance Publication 33 (ITSG-33)

Safeguarding a network in today’s dynamic threat environment is a formidable task. Mobile devices and an increasing dependence on the internet make the job of maintaining control of network systems and data seem nearly insurmountable. The continual discovery of product vulnerabilities and the advent of malware toolkits ensure that networks are continuously bombarded by increasingly sophisticated attacks. Poor asset management, weak configurations, inadequate user access controls, and insufficient network monitoring increase the risk that critical systems and sensitive data will be compromised.
The Communications Security Establishment Canada (CSEC) developed a series of guidelines for security practitioners to manage information technology (IT) security risks for Government of Canada (GC) information systems. The Information Technology Security Guidance Publication 33 (ITSG-33), IT Security Risk Management: A Lifecycle Approach, provides a comprehensive set of security controls that can be used to support a wide variety of business requirements. To support interoperability needs, the ITSG-33 guide is consistent with controls published in the U.S. National Institute of Standards and Technology (NIST) Special Publication 800-53.
Tenable™ has created a series of ITSG-33 dashboards and a report that align with ITSG-33 security controls in the following families:
- AC (ACCESS CONTROL)
- AU (AUDIT AND ACCOUNTABILITY)
- CA (SECURITY ASSESSMENT AND AUTHORIZATION)
- CM (CONFIGURATION MANAGEMENT)
- IA (IDENTIFICATION AND AUTHENTICATION)
- MP (MEDIA PROTECTION)
- RA (RISK ASSESSMENT)
- SC (SYSTEM AND COMMUNICATION PROTECTION)
- SI (SYSTEM AND INFORMATION INTEGRITY)
The goal of ITSG-33 – and of any information security framework – is to provide guidance and direction to help organizations manage risk and protect systems from compromise of confidentiality, integrity, and availability. Failure to effectively manage risk can be costly and damaging to an organization’s business and reputation.
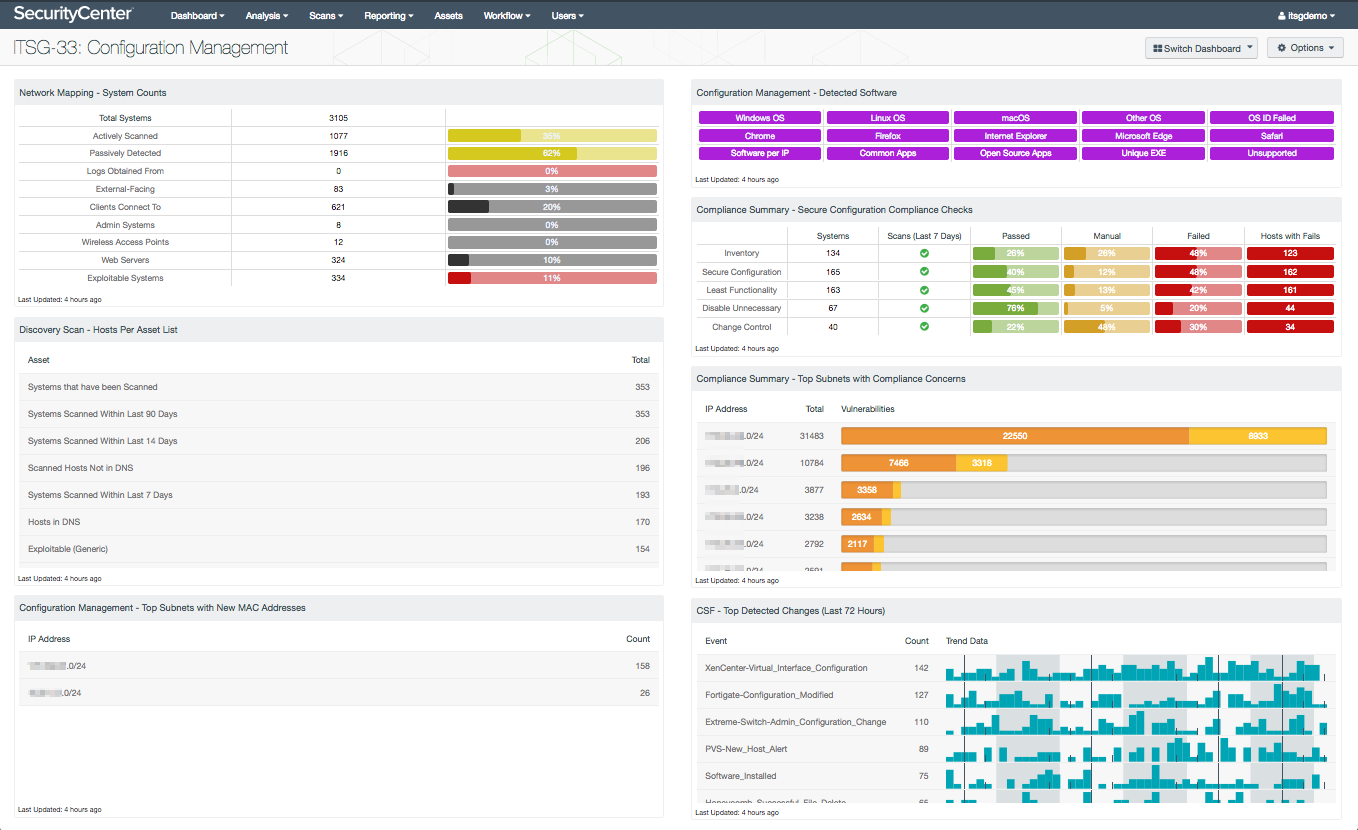
Asset inventory and configuration management
For successful network protection, good asset inventory monitoring and configuration management are required. You can’t protect what you don’t know. If you don’t notice the three servers in a back room that haven’t been patched in two years and that are running end-of-life applications on your network, then your network is at risk.
Tenable SecurityCenter Continuous View® (SecurityCenter CV™) has the ability to actively and passively detect systems on a network. The functions of those systems, as well as what operating systems and other software are running on them, are identified. SecurityCenter CV can collect logs and detect changes such as new machines on the network and software being installed. In addition, SecurityCenter CV supports running compliance or audit scans against systems to assess their configuration security.
This inventory and security configuration information can assist your organization in protecting the network and evaluating your compliance with ITSG-33 security controls, including:
- Configuration Change Control (CM-3)
- Least Functionality (CM-7)
- Information Systems Component Inventory (CM-8)
- User-Installed Software (CM-11)
I find the Tenable ITSG-33: Configuration Management dashboard very helpful to get an overview of configuration management information. Using this dashboard, you can monitor counts of systems, such as wireless access points and web servers, and see the software detected on the network, such as which browsers are in use. The compliance summary information on the dashboard helps you know where to focus security hardening efforts. Detected changes alert you to possible unexpected or unauthorized modifications. To get specifics on hosts or change events, you can drill down into the results. This ability to drill down for further investigation is a particularly useful feature of SecurityCenter CV dashboards.
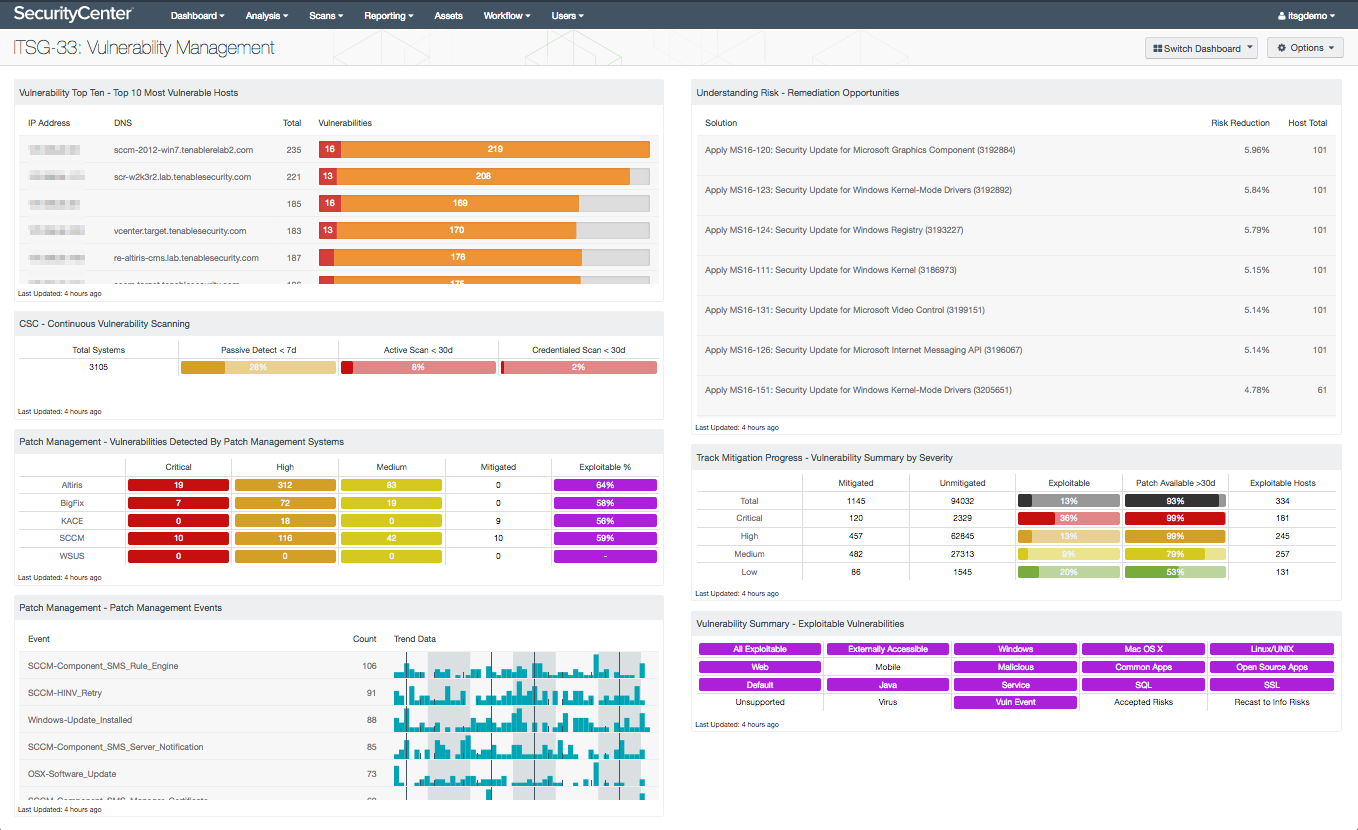
Vulnerability management
Once an accurate inventory is determined and properly configured, an important next step in securing the network is finding and fixing vulnerabilities. Vulnerable devices can be exploited, putting your network and your data at risk. Vulnerability management involves detecting vulnerabilities on network systems, prioritizing which vulnerabilities to deal with first, patching or updating to remediate the vulnerabilities, and monitoring to confirm that the vulnerabilities are fixed.
Effectively managing vulnerabilities is often a challenge due to a lack of time and resources. Fortunately, a core competency of SecurityCenter CV is vulnerability detection. SecurityCenter CV also tracks vulnerabilities, noting vulnerabilities that are not detected on rescans and marking those vulnerabilities as mitigated. SecurityCenter CV can determine the top most vulnerable systems, highlight vulnerabilities known to be exploitable, and present top remediation opportunities, all to assist in prioritizing remediation efforts.
This vulnerability detection and management information can assist your organization in securing the network and evaluating your compliance with ITSG-33 security controls, including:
- Flaw Remediation (SI-2)
- Risk Assessment (RA-3)
- Vulnerability Scanning (RA-5)
What I consider most useful about the Tenable ITSG-33: Vulnerability Management dashboard is that the dashboard makes vulnerability management more measureable, such as by tracking mitigation progress and monitoring vulnerability scanning coverage and recent activity. This dashboard also assists in identifying the top at-risk systems on your network and motivating you to ensure that the necessary organizational resources are applied to best address the vulnerabilities. The exploitable vulnerability indicators are particularly important, to identify known exploitable vulnerabilities that are a high priority to remediate before they can be taken advantage of – this is particularly useful information to act on before a red team assessment! Data from patch management solutions such as SCCM, WSUS, and Symantec Altiris is also included on the dashboard.
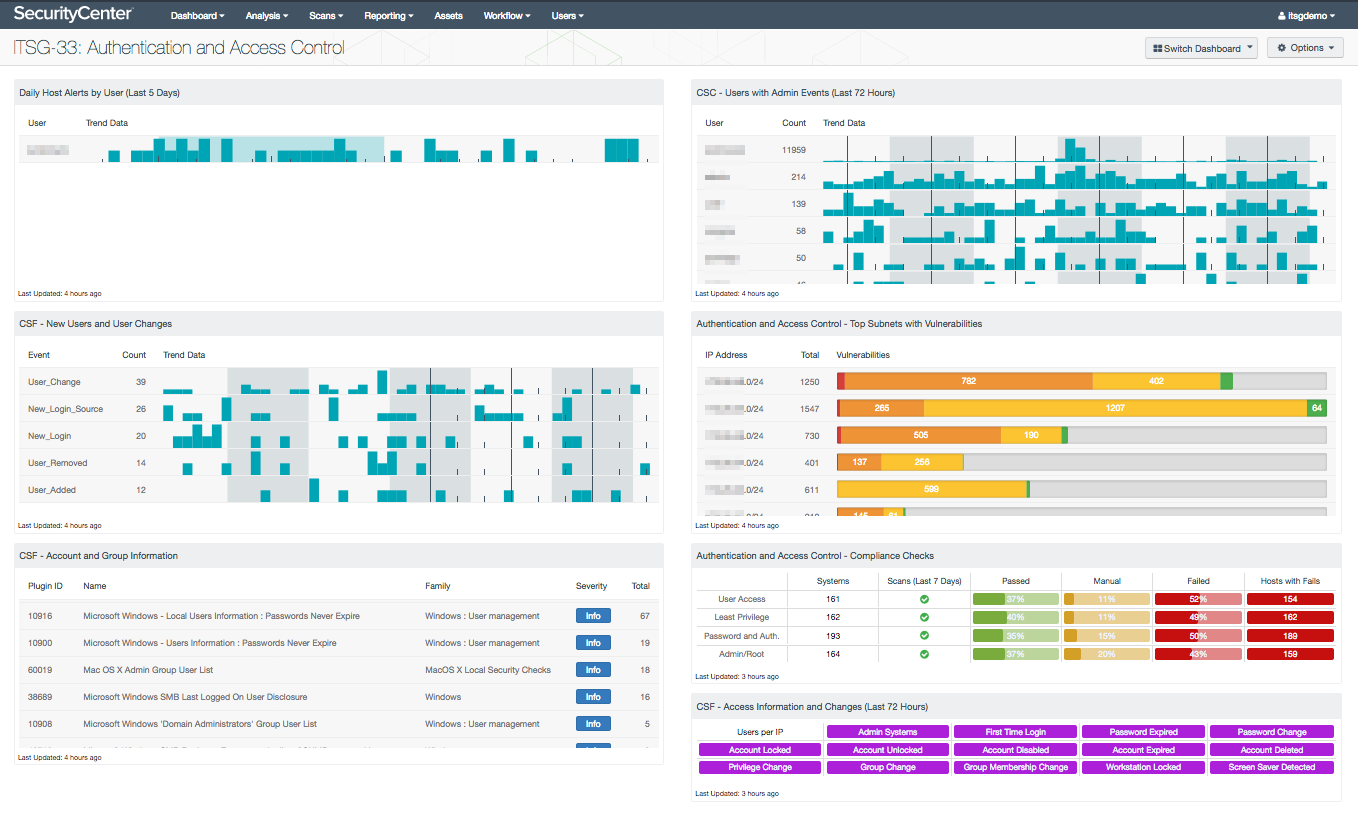
Authentication and access control
Controlling access to systems and data is another vital step in securing a network. Poor authentication and access control opens the door for network intrusion and data theft. Authentication mechanisms must be secure, users must not have more access than they require for their jobs, and suspicious access activity must be detected and investigated.
SecurityCenter CV can assist in this area as well. Authentication vulnerabilities and access control compliance concerns can be detected. User account logins and other user activity can be tracked. Using credentialed scans, SecurityCenter CV can obtain lists of accounts, such as disabled accounts, accounts that have never changed their password, Mac OS X admin group user accounts, and more. In addition, SecurityCenter CV can detect account and group changes, such as new users and privilege changes.
As before, this information can assist your organization in controlling access to your network and evaluating your compliance with ITSG-33 security controls, including:
- Access Enforcement (AC-3)
- Account Management (AC-2)
- Identification And Authentication (IA-Family)
- Least Privilege (AC-6)
- Separation Of Duties (AC-5)
- Session Lock (AC-11)
- Session Termination (AC-12)
- System Use Notification (AC-8)
- Unsuccessful Logon Attempts (AC-7)
The Tenable ITSG-33: Authentication and Access Control dashboard presents useful information to monitor and improve authentication and access control on your network. Knowing the top subnets with authentication and access control vulnerabilities helps you to better understand where the weak points are on your network and focus attention on these areas. You can drill down and see the vulnerability information by IP address or asset list as well. Of course, the ability to monitor account activity is very important to access control. The dashboard lists users who have performed or attempted to perform administrative actions, enabling you to identify any unexpected users who may have too much privilege. New users and access change information alert you to potential suspicious changes that you may need to further investigate.
Additional ITSG-33 resources
Tenable has additional dashboards to support ITSG-33, including Workforce Mobility, Data Protection, Audit and Monitoring, and Audit Details. The Audit Details dashboard in particular presents the results of an ITSG-33 compliance audit by individual security controls. An ITSG-33 Report is available that combines much of the information from the various dashboards into a single report. A related dashboard, Canadian Top 10 Security Actions, based on ITSB-89, is also available.
The information presented in the ITSG-33 dashboards and report can help your organization to better secure and monitor the network, enabling better defenses against attacks and responses to malicious activity, and ultimately safeguarding your critical assets and sensitive data. The dashboards mentioned here are presented in the context of ITSG-33, but many of these dashboards and the security concerns they highlight are generally applicable to any network.
Related Articles
- Government
- Security Frameworks
- SecurityCenter