by David Schwalenberg
June 16, 2015
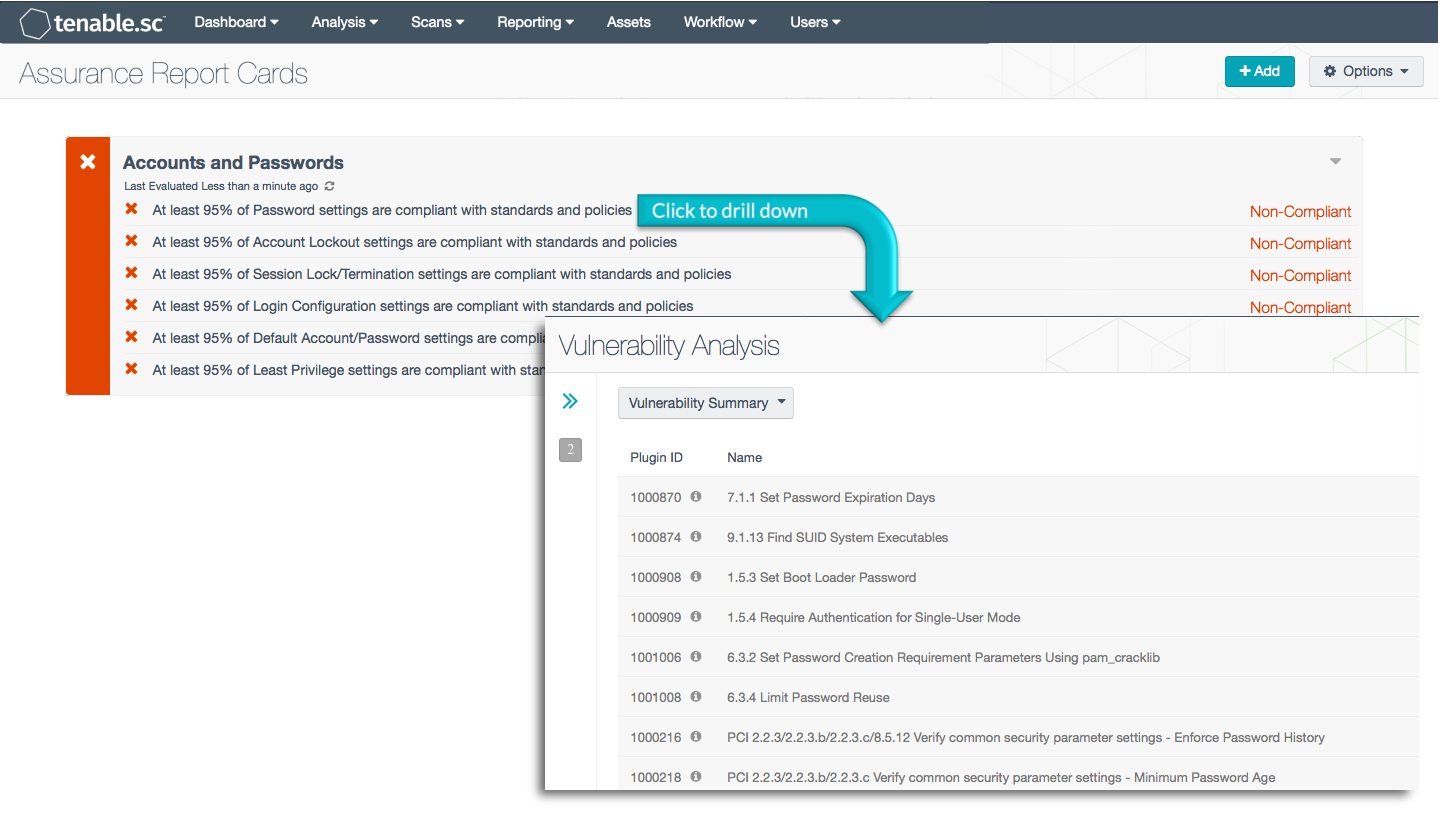
Accounts and passwords that are not compliant with organizational policy based on current accepted standards present great risks to an organization, including the threats of network intrusion and data disclosure. The Accounts and Passwords Assurance Report Card (ARC) presents policy statements that measure percentage compliance against organizational policies such as password policy, account lockout policy, and least privilege policy. Organizational policy will be based on appropriate current accepted standards. This ARC makes use of standards such as NIST 800-53, DoD Instruction 8500.2, and the PCI Data Security Standard to highlight compliance failures relating to accounts and passwords, all the way from password length and complexity requirements to default account and least privilege concerns. This information will allow the Compliance Manager to continuously monitor account and password compliance settings, so that weak policies can be identified and corrected and the network made more secure.
More details on each of the policy statements included in the ARC are given below. The Compliance Manager can click on a policy statement to bring up the analysis screen to display details on any compliance failures related to that policy statement. In the analysis screen, setting the tool to IP Summary will display the systems on which the compliance failures are present.
This ARC relies on audit results obtained from Nessus scans of the systems on the network using appropriate audit files. The descriptions of the policy statements below include information on what details are used to find those audit checks relevant to the policy statement and what the percentage pass rate must be to be considered compliant. The audit files and ARC policy statement parameters are guides that can be customized as necessary to meet organizational requirements.
This ARC is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The ARC can be easily located in the Feed under the category Compliance. The ARC requirements are:
- Tenable.sc 5.0.0.1
- Compliance data
Tenable.sc Continuous View (Tenable.sc CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable's Nessus Network Monitor (NNM), as well as log correlation with Tenable's Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network, in order to best measure compliance against complex standards.
ARC Policy Statements:
At least 95% of Password settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Password settings have passed. Password settings may include password length, complexity, and age requirements, among other things. Compliance is measured against those policy checks that reference one or more of the following standards:
- NIST 800-53 control IA-5 (AUTHENTICATOR MANAGEMENT)
- DoD Instruction 8500.2 control IAIA (Individual Identification and Authentication)
- PCI DSS requirement 8.2 (Ensure proper user-authentication management)
At least 95% of Account Lockout settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Account Lockout settings have passed. Account Lockout settings may include failed logon counts and lockout duration requirements, among other things. Compliance is measured against those policy checks that reference one or more of the following standards:
- NIST 800-53 control AC-7 (UNSUCCESSFUL LOGON ATTEMPTS)
- SANS/Council on CyberSecurity Critical Security Control 16-9 (Account Monitoring and Control: Lockouts)
- DoD Instruction 8500.2 control ECLO (Logon)
- PCI DSS requirement 8.1.6 (Limit repeated access attempts by locking out the user)
- PCI DSS requirement 8.1.7 (Set the lockout duration)
At least 95% of Session Lock/Termination settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Session Lock/Termination settings have passed. Session Lock/Termination settings may include screen lock and idle time requirements, among other things. Compliance is measured against those policy checks that reference one or more of the following standards:
- NIST 800-53 control AC-11 (SESSION LOCK)
- NIST 800-53 control AC-12 (SESSION TERMINATION)
- SANS/Council on CyberSecurity Critical Security Control 16-5 (Account Monitoring and Control: Auto logout)
- DoD Instruction 8500.2 control PESL-1 (Screen Lock)
- PCI DSS requirement 8.1.8 (Idle session requires re-authentication)
At least 95% of Login Configuration settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Login Configuration settings have passed. Login Configuration settings may include auditing and banner requirements, among other things. Compliance is measured against those policy checks that include the words "logon" or "login".
At least 95% of Default Account/Password settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Default Account/Password settings have passed. Default Account/Password settings may include requirements to disable default accounts and limit use of blank passwords, among other things. Compliance is measured against those policy checks that include the words "default account", "default admin", "default credential", "default password", "blank password", "null password", "unpassworded", or "passwordless".
At least 95% of Least Privilege settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Least Privilege settings have passed. Least Privilege settings may include requirements to disable certain rights and privileges for specific users, among other things. Compliance is measured against those policy checks that reference one or more of the following standards:
- NIST 800-53 control AC-6 (LEAST PRIVILEGE)
- SANS/Council on CyberSecurity Critical Security Control 12 (Controlled Use of Administrative Privileges)
- SANS/Council on CyberSecurity Critical Security Control 15 (Controlled Access Based on the Need to Know)
- SANS/Council on CyberSecurity Critical Security Control 16 (Account Monitoring and Control)
- DoD Instruction 8500.2 control ECLP (Least Privilege)